SOC 2 Compliance Simplified for Busy Tech Executives






Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Ron has to choose from two startups.
Both offer identical services at significantly different price points. Out of the two, only startup B is certified in security compliance. As the CTO of an enterprise firm, evidence of being able to protect his organization’s data from breaches is crucial to Ron.
So despite startup A’s lower price, he chose startup B:
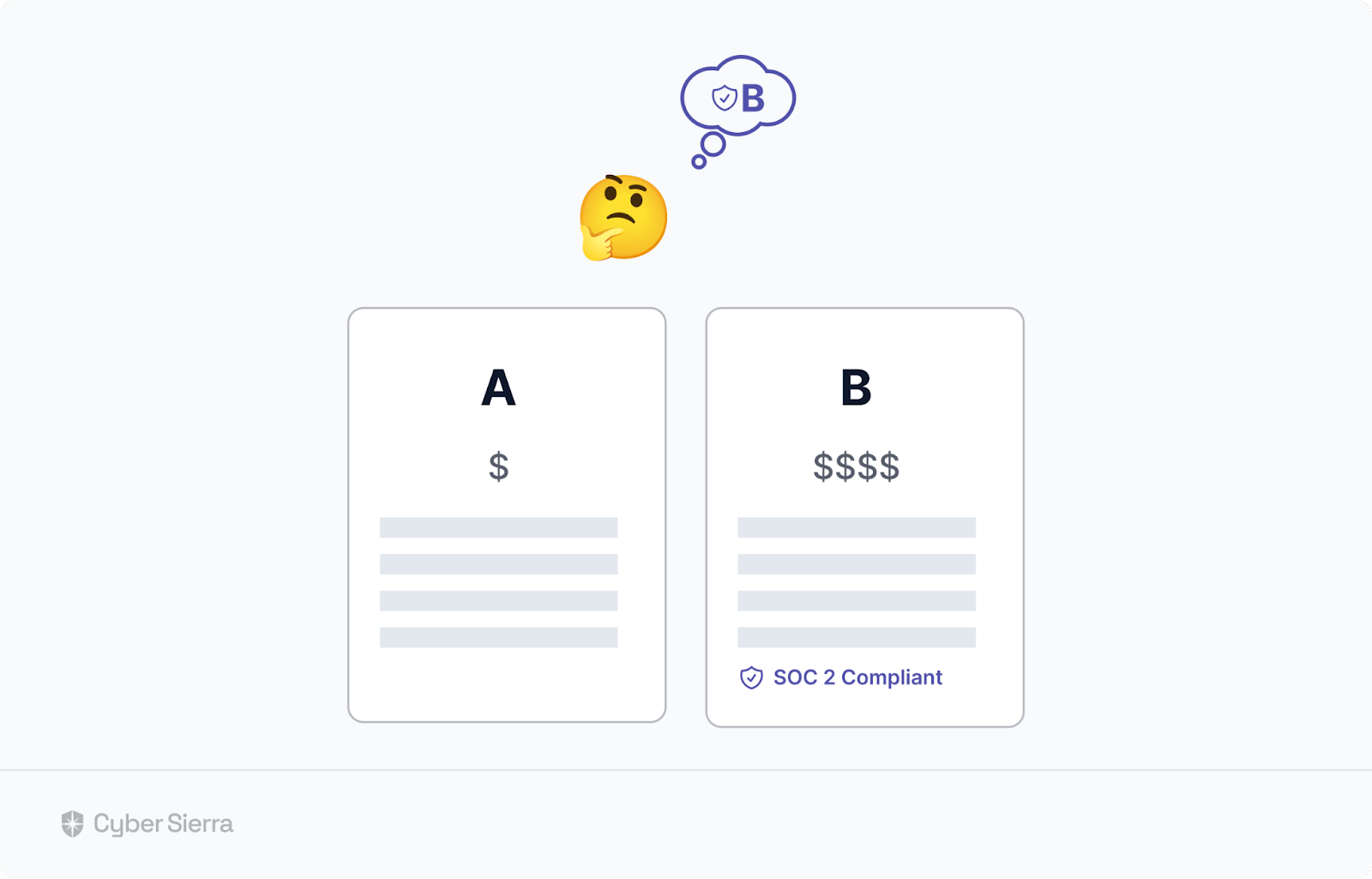

This scenario highlights just one advantage of being SOC 2 compliant. It makes prospects see your growing startup as a security-conscious partner, giving you an edge in competitive enterprise deals.
But meeting requirements and passing independent CPA audits to achieve SOC 2 compliance is no easy feat. To increase your chances…
Early Preparation for a SOC 2 Audit is Key
A Cybersecurity Writer at CSO said it best:
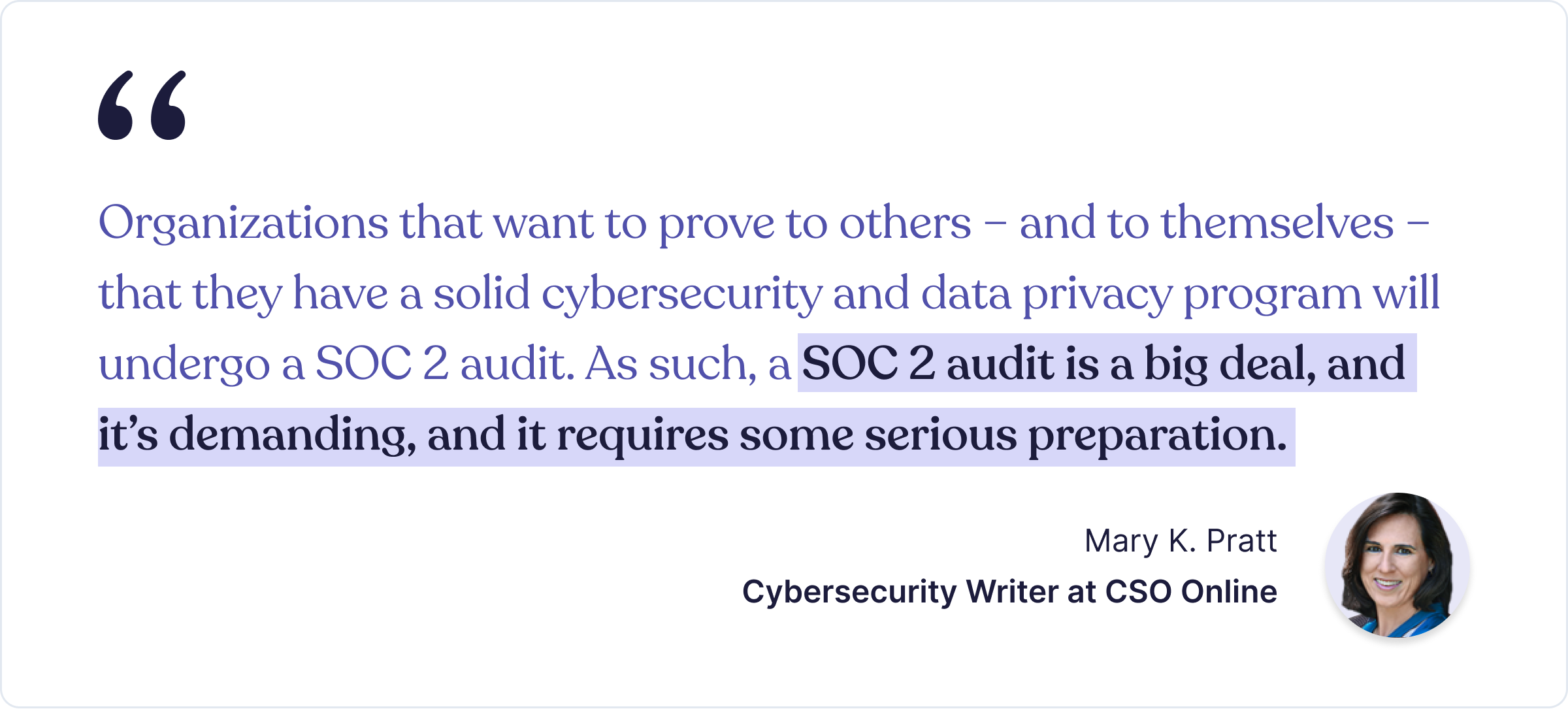

Demanding tasks are simplified if broken into small steps. Since the same applies to earning SOC 2 attestation, an optimal early preparatory path is knowing what steps to take.
Some crucial ones include:
- Having the core SOC 2 compliance requirement in place
- Creating a checklist to help you automate the process
- Knowing how much a SOC 2 report will cost you.
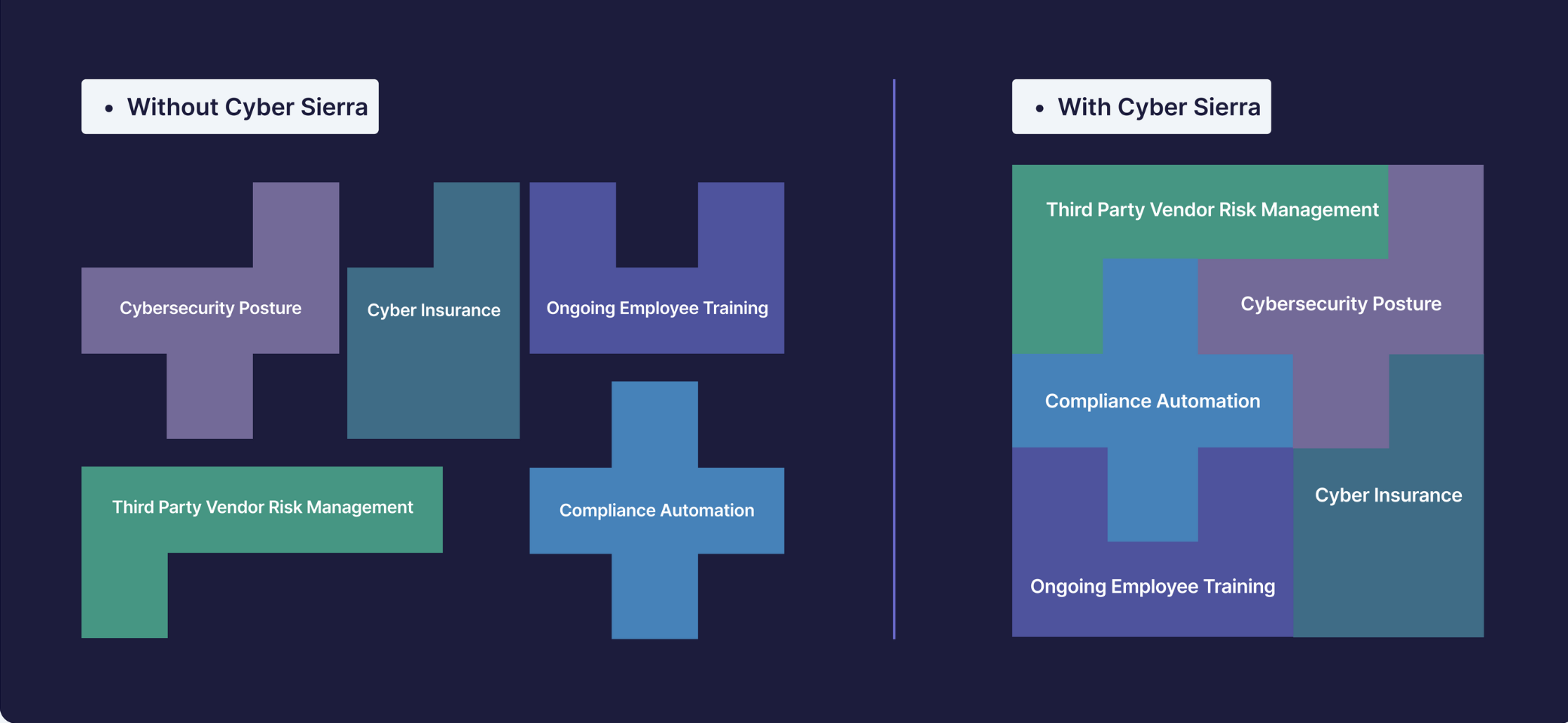
To help you prepare and ace the audit, this guide will explore these steps. You’ll also see how to build a solid cybersecurity posture and automate the SOC 2 compliance process with Cyber Sierra:




Improve your company's cybersecurity posture and automate SOC 2 compliance processes from one place.

The Core SOC 2 Compliance Requirement
SOC 2 compliance has two types.
And requirements depend on the one you seek. SOC 2 Type I checks if you are SOC 2 compliant at a particular point in time. It’s like a snapshot. Type II, on the other hand, reviews your company’s cybersecurity compliance over a longer period (i.e., have you been compliant in 6–12 months?)
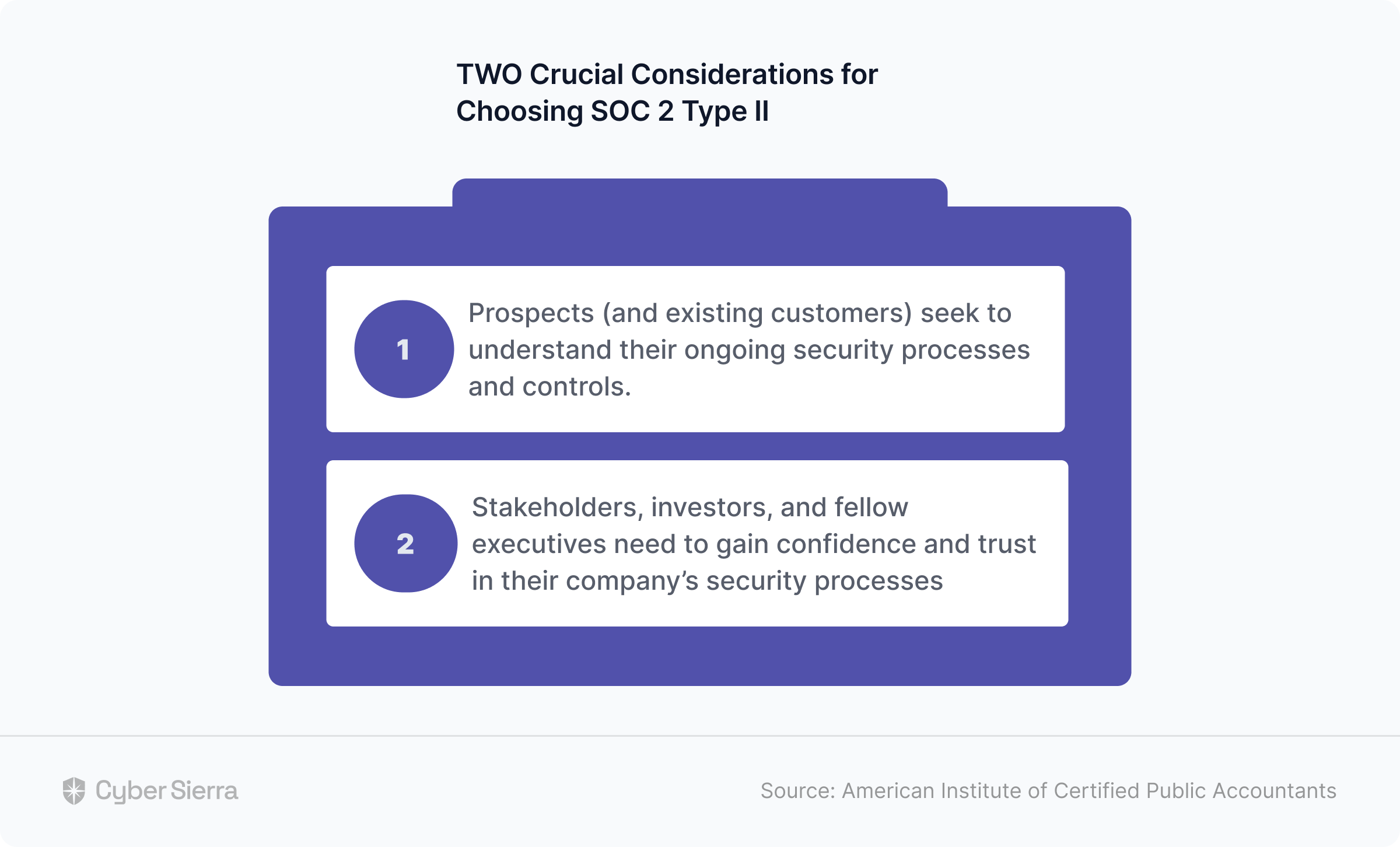
Per the American Institute of Certified Public Accountants (AICPA), the organization behind this compliance certificate, companies should consider a SOC 2 Type II report when:
- Stakeholders, investors, and fellow executives need to gain confidence and trust in their company’s security processes.
- Prospects (and existing customers) seek to understand their ongoing security processes and controls:

SOC 2 Type II is therefore more comprehensive, carries more weight, and is the one often requested by security-conscious prospects. Getting it revolves around AICPA’s five Trust Services Criteria (TSC):
- Security,
- Availability,
- Processing integrity,
- Confidentiality,
- Privacy.
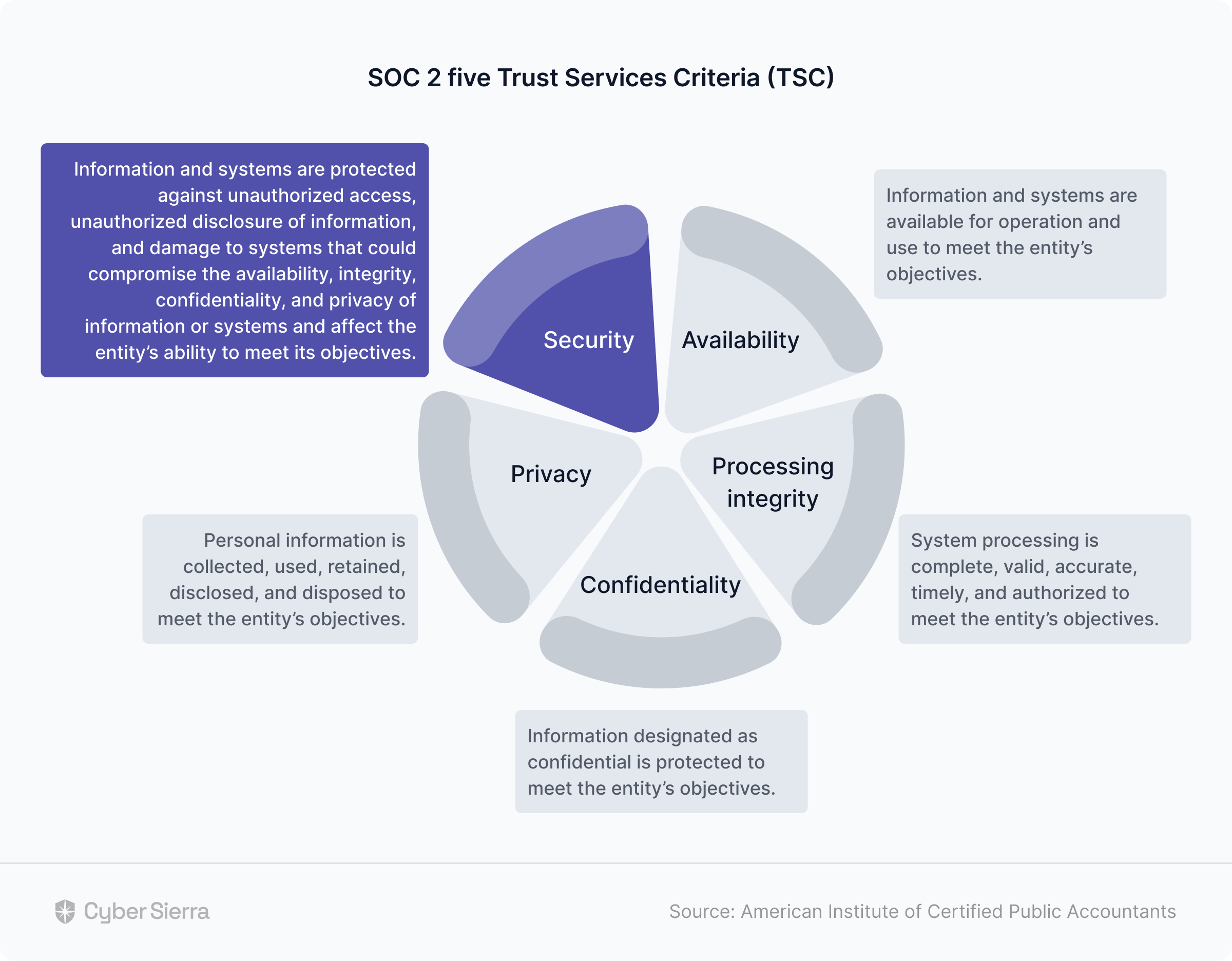

Out of these five, security is the core and compulsory.
And veteran CPA, Bernard Gallagher, stressed why:


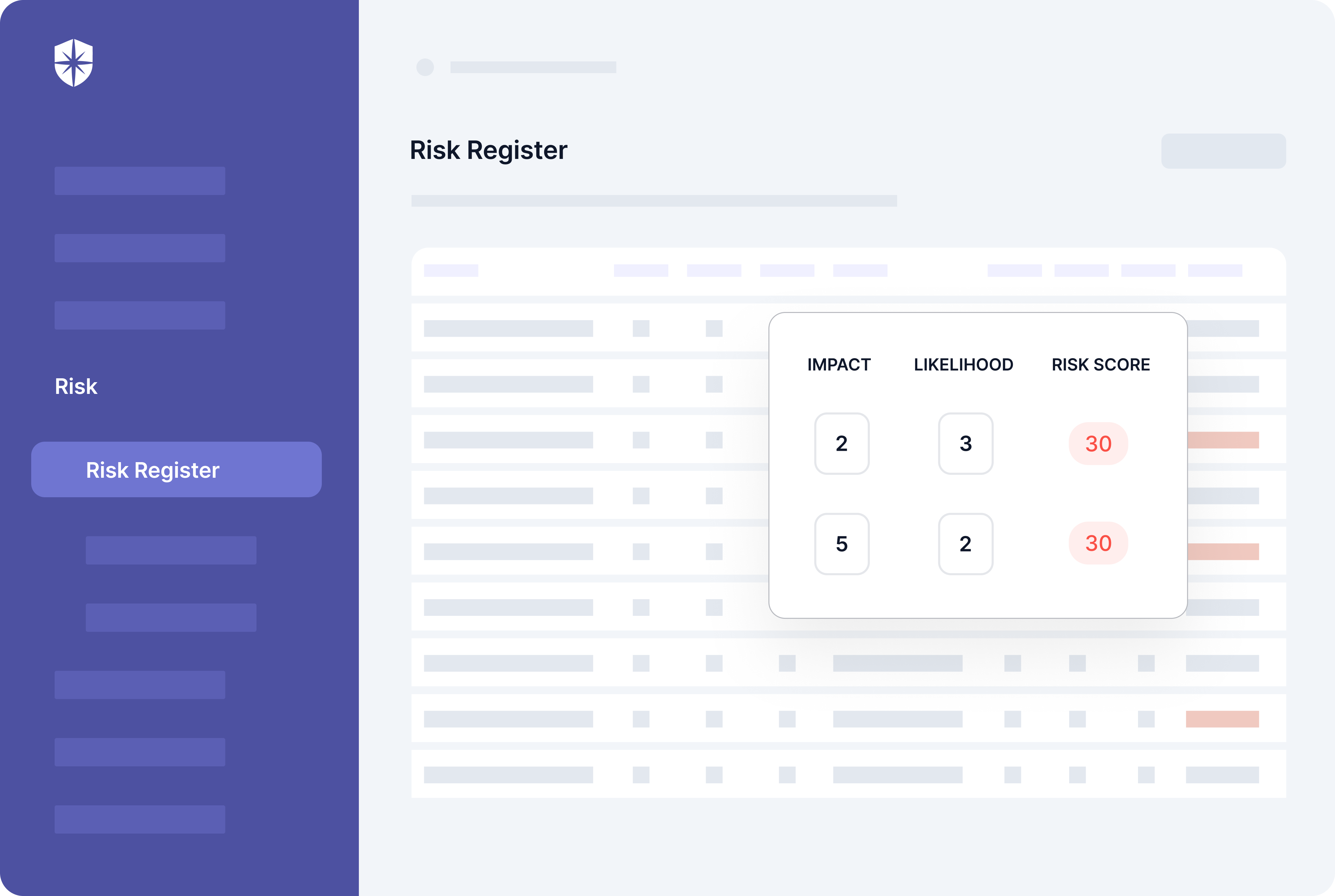
In other words, to appease SOC 2 Type II auditors, you must prioritize managing security risks effectively across your organization. For this, consider a cybersecurity platform that can:
- Automatically scan your cloud assets
- Detect risks and vulnerabilities in real-time
- Assess and score the impact of those risks, and
- Enable you to assign remediation tasks to relevant members of your security team from one risk register.
You can do all these with Cyber Sierra’s Risk Register:


But it doesn’t end there.
Ongoing employee security awareness training is also a core requirement of SOC 2 Type II. This means you must continuously train employees to remain compliant when it’s time for audits again.
SOC 2 Compliance Checklist, Automation Guide
Many CTOs and IT executives have become SOC 2 compliant in record time through our interoperable cybersecurity platform. For some, the scenario (recall this blog’s intro?) of startup A losing a big deal to startup B for not having security compliance is common.
We believe no startup should suffer that.
So based on our experience working with numerous businesses to automate the various processes involved, we’ve created this SOC 2 compliance checklist for your reference.
1. Scope Your SOC 2 Project Plan
A crucial first step is ensuring team members get the same sense of priority as you journey towards becoming SOC 2 compliant. You don’t want them treating tasks related to it as just another to-do.
So start the project with a description that addresses:
- Why your startup needs SOC 2 compliance.
- How it will bolster your company’s security posture.
- The type of SOC 2 audit you’re going for (and why).
Still in the scoping step, outline and briefly explain components within your org that must meet AICPA’s attestation standards. They include infrastructure, data, procedures, software, and people.
The TSC that applies to your business is next.
As stated earlier, security is the core SOC 2 requirement, so it must be included in your scope. Selecting other TSCs should be based on demands and regulations pertinent to your organization.
For instance, choose:
- Availability if prospects and existing customers have concerns about your product’s downtime.
- Confidentiality if prospects and customers have specific requirements for confidentiality or if your startup stores sensitive info protected by NDAs (non-disclosure agreements).
- Processing Integrity if your company executes critical operations like financial processing, tax processing, payroll services, and related ones.
- Privacy if prospects and existing customers store PII (personal identifiable information) like birthdays, healthcare data, and social security numbers.
2. Implement SOC 2 Policies and Procedures
Across the five TSCs, there are:
- 26 mandatory policies, and
- About 196 security controls.
Defined procedures for implementing the policies and their respective security controls that apply to your organization are needed. Typically, this requires expertise and involves a lot of manual work.
You need:
- The expertise to know what policies to prioritize
- Lots of manual work uploading evidence of security controls for each policy, which can be draining for everyone involved.
This is where technology comes in.
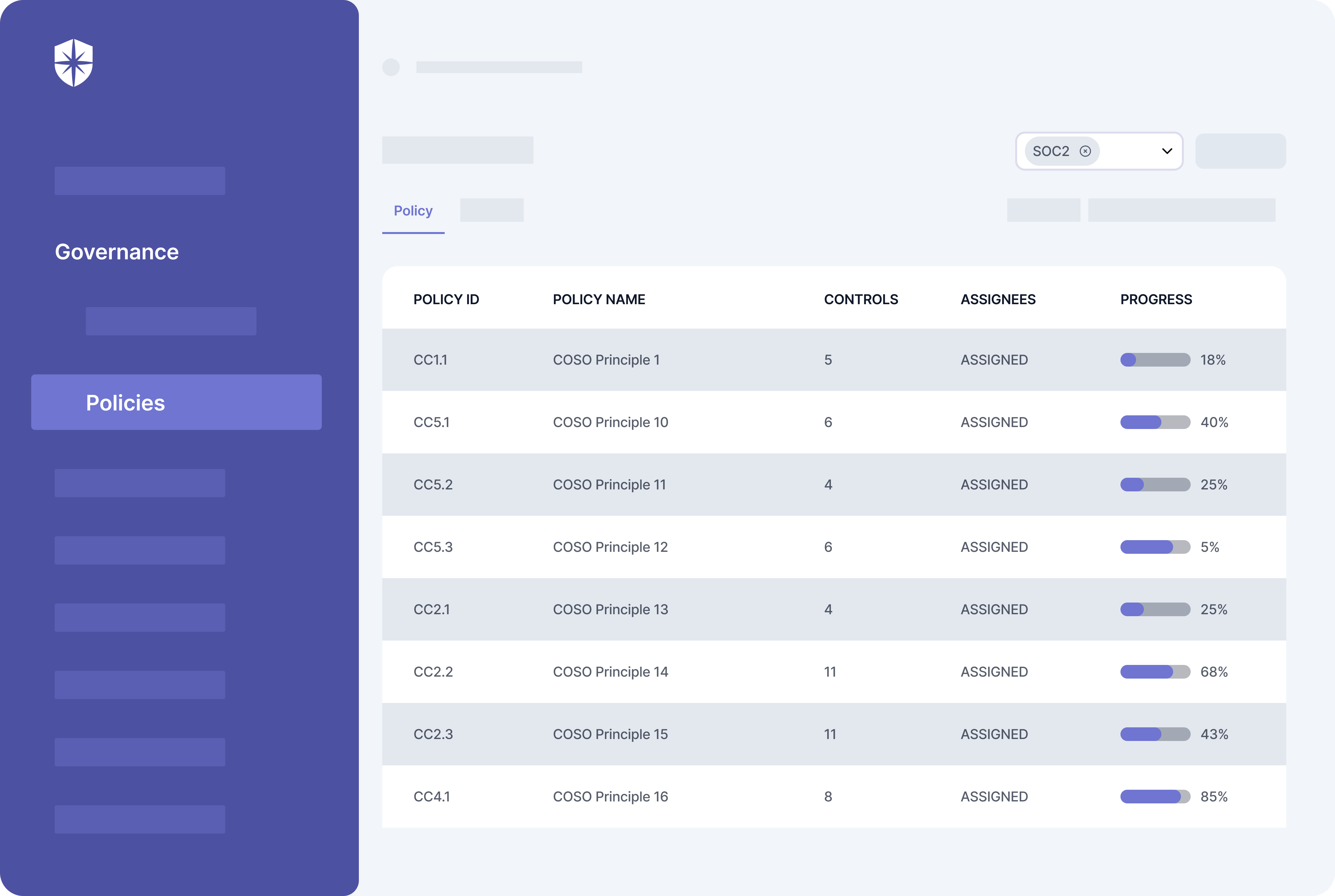
With Cyber Sierra, for instance, ticking this step off your SOC 2 checklist is easy. There’s an expert to help you choose the mandatory policies you should prioritize. Our technology also has these policies and security controls built into it and updated regularly.
So from one dashboard, you can:
- Assign policies (and their controls) to relevant team members
- Track their progress in implementing those controls:

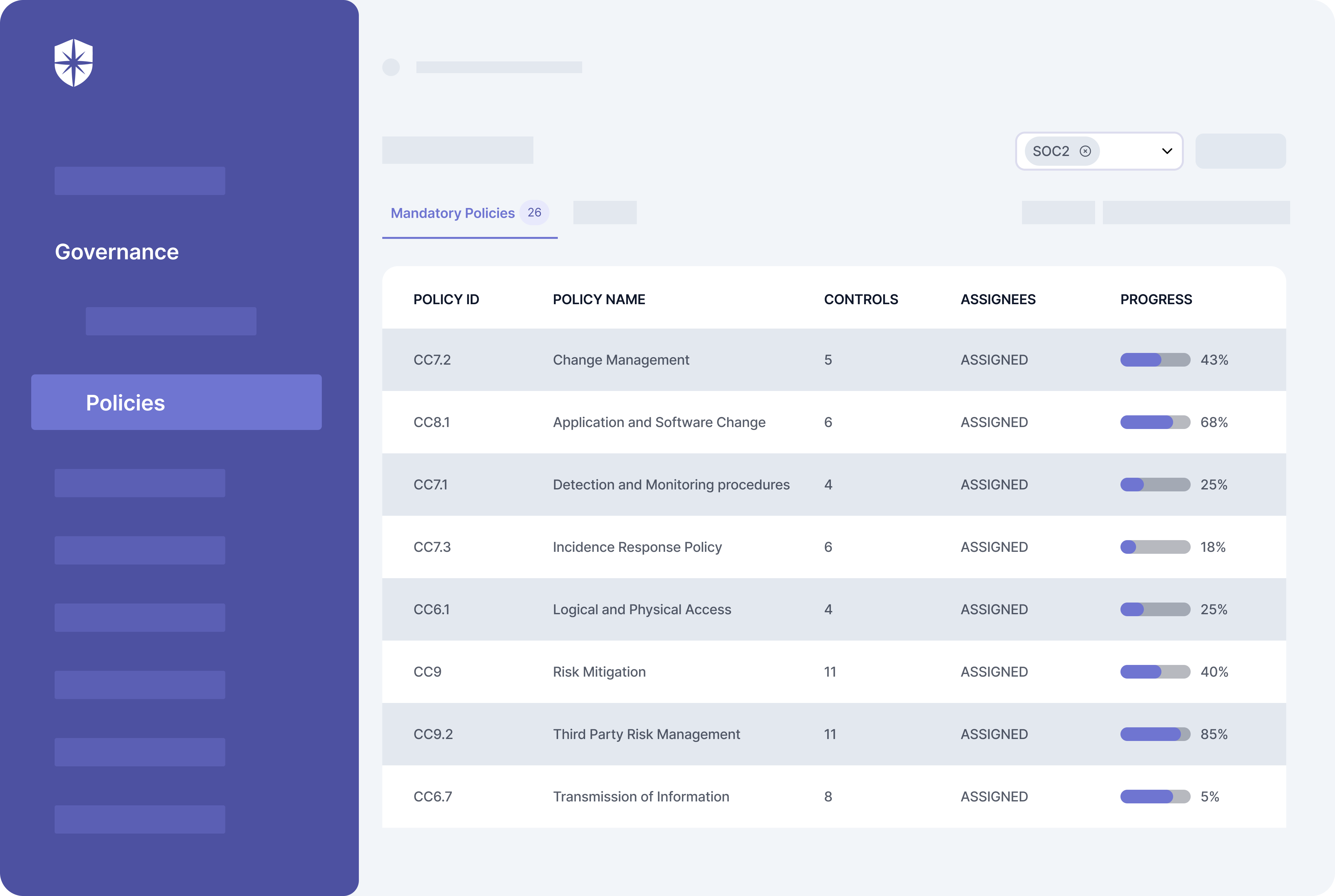
3. Complete SOC 2 Compliance Documentation
Is there evidence to show that your company has implemented security controls for policies based on the chosen TSC?
Saying ‘yes’ isn’t enough.
To pass auditors’ scrutiny and earn SOC 2 compliance, you must show proof by uploading appropriate documentation. The final number of documentation you’ll need to provide to a CPA depends on the TSC chosen in the scoping step.
However, as with TSC, there are mandatory ones like:
- Change Management
- Application and Software Change
- Data and Software Disposal
- Detection and Monitoring Procedures
- Incidence Response Policy
- Logical and Physical Address
- Third Party Risk Management
- Risk Mitigation.
The procedures for providing evidence of security controls for each required documentation above are also built into Cyber Sierra:

And it doesn’t end there.
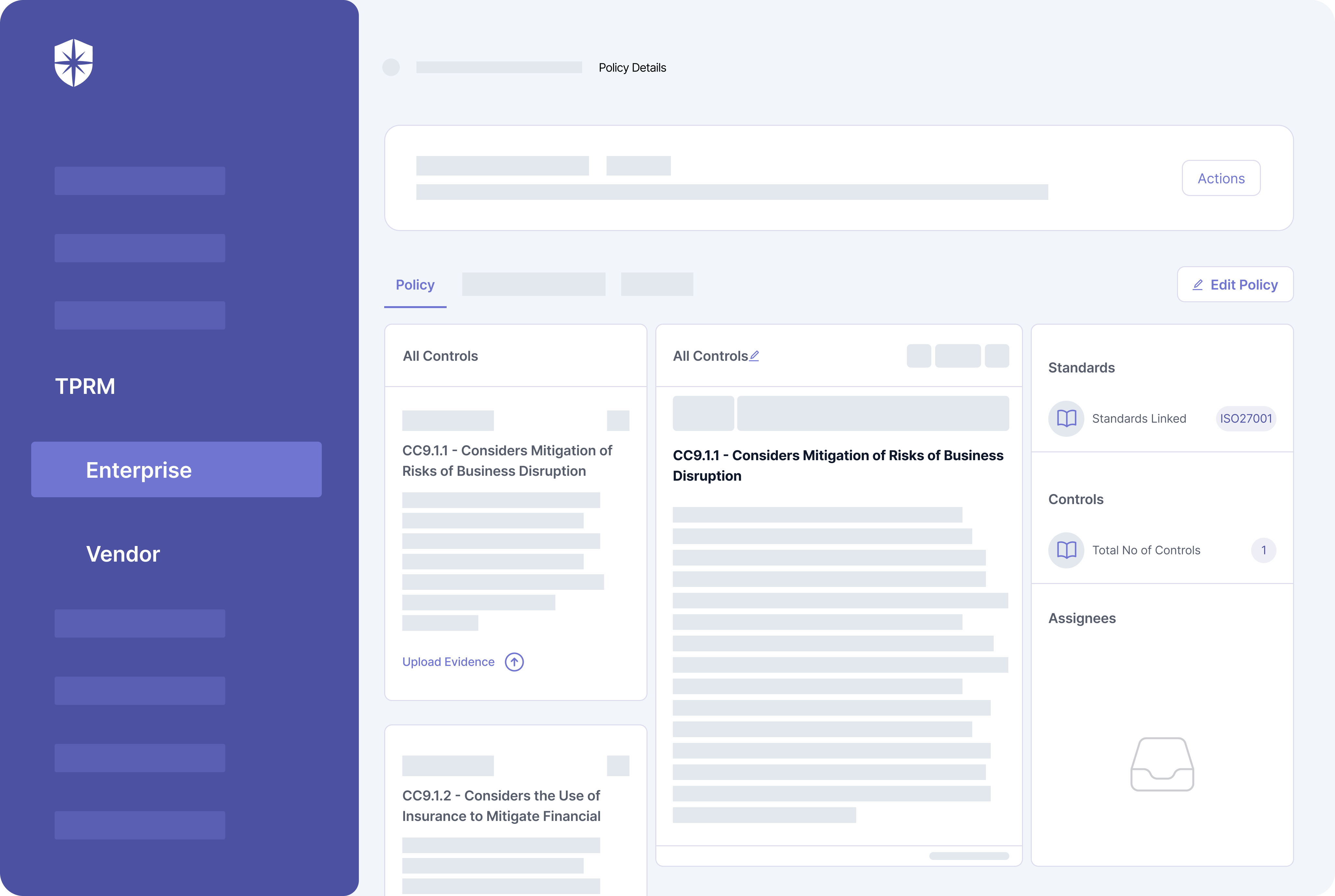
Cyber Sierra also simplifies the process of uploading evidence for the compulsory SOC 2 documentation and TSC security controls. For instance, click on any policy, say, Risk Mitigation, and in addition to succinct descriptions of what it (and its controls) entails…
You can edit a policy per your needs and upload evidence:

4. Conduct SOC 2 Readiness Assessments
This step comes down to two things:
- An internal risk assessment to ensure that cyber posture and uploaded security controls’ evidences are accurate.
- Remediation of identified risks and vulnerabilities, ensuring your organization is ready to pass strict SOC 2 audit reviews.
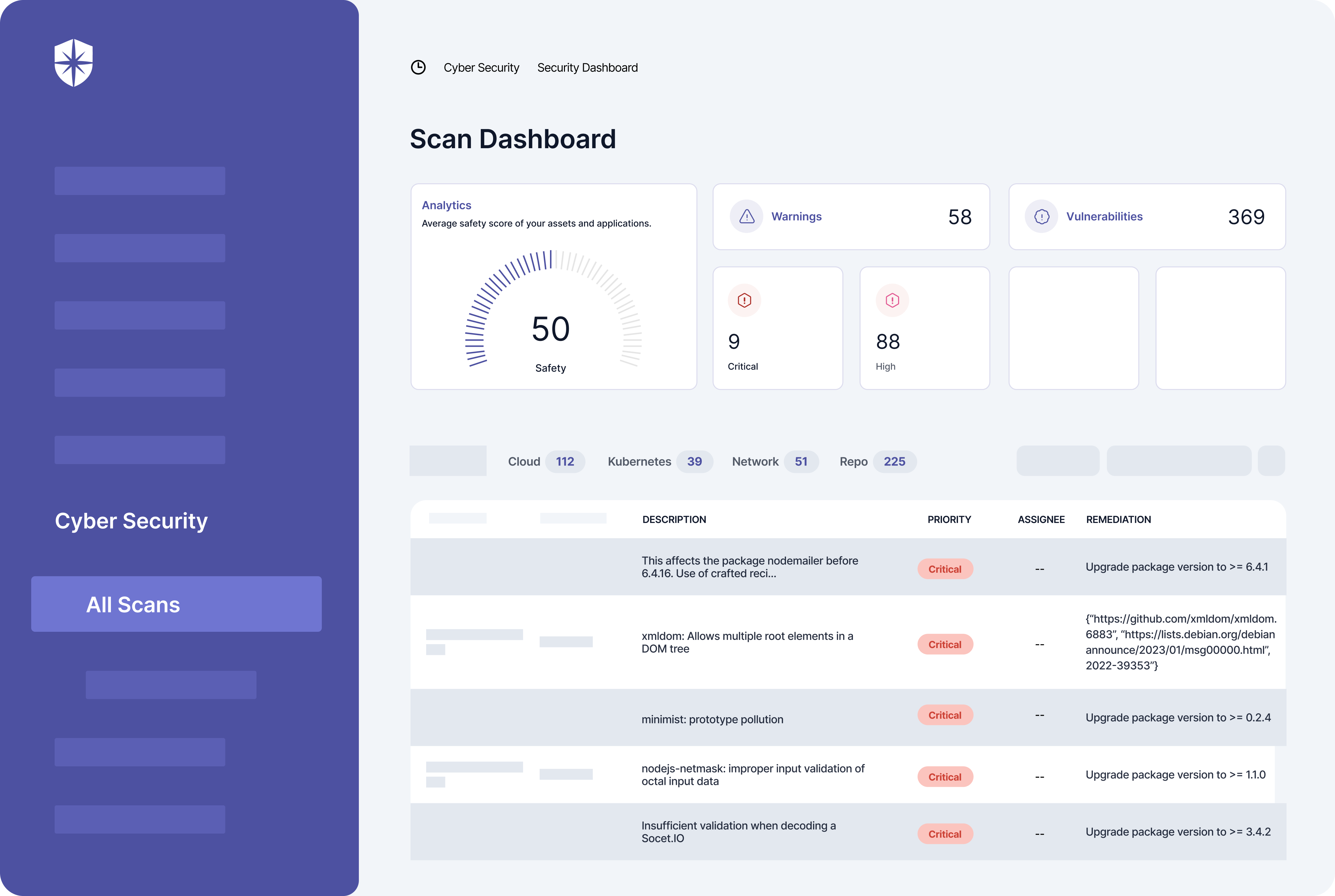
Ticking both off your SOC 2 checklist starts with scanning your cloud assets and network environments to identify vulnerabilities. Then, remediating each to boost your confidence of passing the audit.
Cyber Sierra automates both.
In a few clicks, you can connect and scan your cloud, repository, Kubernetes, and network environments. Each scan prompts a dashboard with your company’s cybersecurity posture, from where you’ll find all vulnerabilities and descriptions of critical risks.
You also get instructions on how to remediate each vulnerability and can assign remediation tasks to relevant people on your security team:

5. Monitor Security Controls for Upto 12 Months
Adhering to the four steps above snapshots your company’s cybersecurity posture. They are enough for SOC 2 Type I audit reviews. But for SOC 2 Type II certification that’s often-requested by prospects and customers, you must be compliant for up to 12 months.
So you must continuously monitor for at least 12 months to ensure evidence uploaded for each security control is intact. This boils down to detecting, assessing, and remediating risks that could render the evidence you upload for security controls worthless.
Technology can simplify this process.
For instance, and as I shared earlier, connect your tech stack to a good cybersecurity platform, and it will:
- Automatically scan your cloud assets
- Detect risks and vulnerabilities in real-time
- Assess and score the impact of those risks, and
- Enable you to assign remediation tasks to relevant members of your security team from one risk register.
Again, Cyber Sierra’s Risk Register does these out of the box:



How Much Does SOC 2 Report Cost?
SOC 2 compliance is a huge undertaking.
Hiring an auditor for the review alone starts at about $5k and could exceed $30k, depending on the auditing company. It doesn’t end there. In no particular order, you’ll also incur costs to:
- Scope and manage the project
- Train employees on cybersecurity awareness
- Train security team members on remediating risks
- Commission legal review of uploaded documentation
- Perform readiness assessments and ongoing monitoring of security controls of chosen policies.
- Manage third-party vendor risks.
Depending on company size, these steps could take 6–12 months and can cost $50-$110k in lost time and productivity if done manually. On the flip side, these costs reduce drastically if your team can manage and automate most of the requirements above from one place.
And that’s why we built Cyber Sierra:




A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.