How To Spot A Phishing Email





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Email phishing has become one of the most typical starting points of cyber breaches because every employee deals with emails daily.
These attacks have severe effects on organizations, leading to financial losses, reputational damage, and compromised security. Therefore it’s important to stay alert and educate employees on the various phishing techniques and apply security measures to avoid being a target of these attacks.
In this article, we will explain how to identify phishing emails and provide tips to equip you with the knowledge and skills necessary to identify and combat email phishing threats effectively.


What is email phishing?
Email phishing is a form of cyber attack where attackers hide their true identity and deceive individuals to perform an action for malicious purposes via emails.
These emails are designed to look like they came from an authorized bank, government office, or organization. In these emails, the attackers typically ask the recipient to click on a link that will redirect them to a page where they’ll be asked to confirm sensitive details, such as personal data or account information.
If the recipient falls prey to this and reveals sensitive information, the attacker will exploit it for financial gain, identity theft, or launch additional attacks. Such types of attacks are successful because they use human vulnerabilities rather than technical loopholes in a system or software.
What is the purpose of a phishing attack?
The purpose of a phishing attack is to deceive a person or an organization to get sensitive details, such as personal information, login credentials, or financial data. Here are the most common reasons why phishing attacks are carried out:
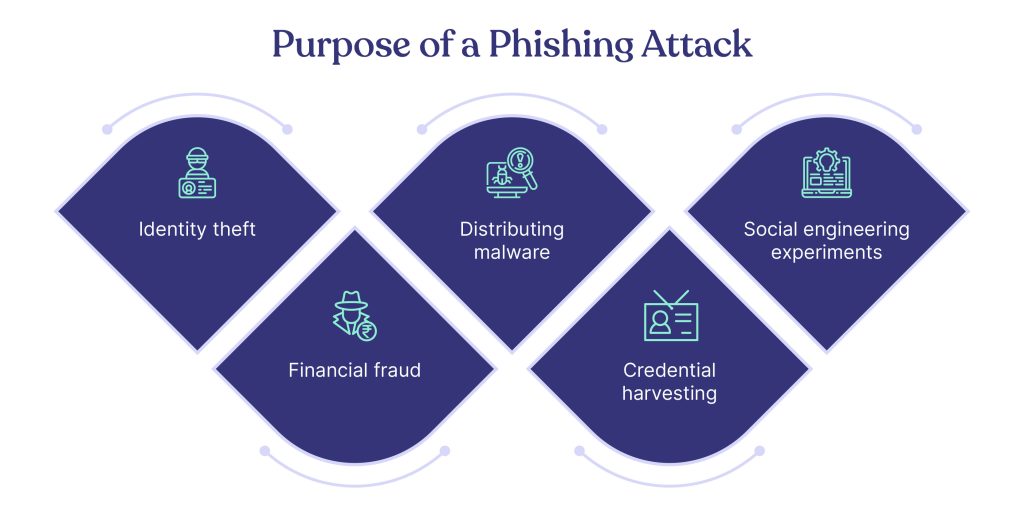

- Identity theft – To steal personal information such as government identification numbers, birth dates, or social media credentials. This information can be used to open fake accounts, damage reputation, obtain free medical care or indulge in other criminal activities.
- Financial fraud – Phishing attacks also trick individuals into revealing credit card information, and banking details. This information is used for unauthorized transactions and empty bank accounts.
- Distributing malware – Phishing emails often carry malicious attachments or links. When the victim clicks or downloads them, malware gets installed on their device. This can be used to collect personal or business information to carry out other malicious activities.
- Credential harvesting – These emails target specific organizations or services to gather login information en masse. These credentials are then sold in the black market or used for subsequent attacks.
- Social engineering experiments – Some phishing attacks are also used by hackers for research purposes to test security understanding, vulnerabilities, or response actions within organizations.
Phishing attacks: revealing the alarming statistics
Top Phishing Attacks Statistics 2023
- 92% of organizations were victims of phishing in the past 12 months – Source
- The average cost of a data breach with phishing is USD 4.91 million – Source
- 36% of all data breaches involved phishing – Source
- The subject line for 67% of spam emails is empty – Source
How to identify a phishing email?
Identifying phishing emails can be tricky because attackers are increasingly using sophisticated methods. However, by paying attention to certain indicators, you can spot the phishing attempt. Here’s a breakdown of the standard indicators of a phishing attack:
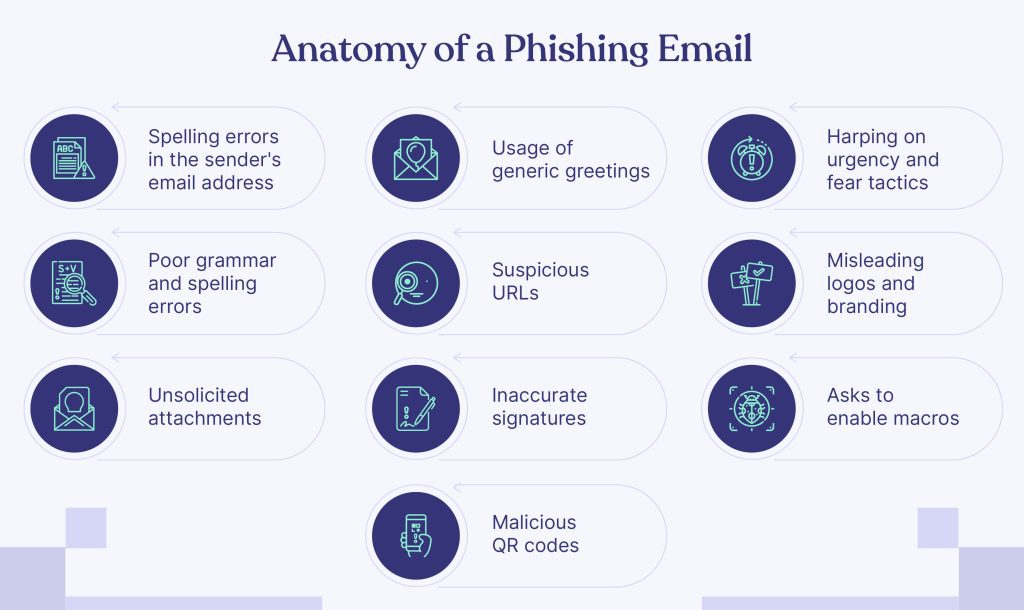

- Spelling errors in the sender’s email address – Phishing attackers impersonate a legitimate organization to make it look real. But they will often have slight variations and spelling errors. Plus, they will be sent through a free email service provider rather than the registered company domain
- Usage of generic greetings – Attackers will use greetings such as “Dear customer” or “Dear sir/madam” instead of using your name. Legitimate organizations will use your name to make it more personalized
- Harping on urgency and fear tactics – Phishing emails create a sense of urgency to take steps without any delay. Attackers might say your account is compromised, you’ve won a prize, or promise perks like fake discounts.
- Poor grammar and spelling errors – Phishing emails typically have more grammar and spelling mistakes. While legitimate organizations can also make errors, an excessive number of errors is always a red flag
- Suspicious URLs – Links will often lead to unsafe websites that are designed to collect your personal information. Sometimes even the website domain name will be misspelled. To view the actual URL, you can always hover over the URL without clicking it.
- Misleading logos and branding – Company logos, and other branding elements will not be authentic. They will be low in quality, distorted, or slightly altered. You can compare them with the organization’s official website to find similarities.
- Unusual email formatting – These emails will have strange font styles, uneven spacing, or excessive use of exclamation marks. They will lack the professional appearance that can be found in legitimate organizations.
- Unsolicited attachments – Malicious attachments will be masked as an invoice, a delivery note, or something else that motivates you to open it. You must remember that authentic organizations do not randomly send email attachments. Instead, they will redirect you to materials or a guide to download documents from their official website. So, before you click on any such attachment, in case you’re doubtful, it’s good practice to confirm it with the official organization.
- Inaccurate signatures – Legitimate email senders will always add important information to their email signatures. If the signature looks inaccurate, it’s mostly a spam email.
- Asks to enable macros – If the sender asks you to enable macros before downloading a Word document, never trust the email because it is a common medium for ransomware infections
- Malicious QR codes – Attackers can design fake QR codes that look legitimate but lead to malicious websites. You can check if the QR code is from a trusted source, or use a QR code scanner app to check if the QR code you’re about to scan is legitimate
How to defend against phishing attacks?
You cannot prevent a phishing attack; in today’s digital age, they are commonplace. You can, however, defend against one by using a combination of security measures and employee awareness. Here are some ways to protect yourself from phishing attacks.


- Implement security awareness training – Employees are your organization’s first line of defense. So, it’s critical you provide regular security awareness training for them so that they can identify phishing emails, avoid social engineering tactics, and report suspicious incidents. Besides, security training is an important component of getting cybersecurity compliance certifications. Cyber Sierra’s Security Training feature on its platform is more than just a one-time seminar. It is a comprehensive and dynamic program that undergoes regular updates to address the latest threats and industry best practices. More on that later.
- Beware of emails from unknown senders – Be careful of messages from unknown senders or suspicious sources. Do not click on links or download files from such types of emails. As a practice, confirm the authenticity of the sender before taking any actions.
- Verify the legitimacy of websites – When visiting websites, double-check the website’s URL for HTTPS encryption. You also need to check for misspellings or alterations with the domain name.
- Implement email filters and spam detection – Make use of spam filters and email security software so you can block such emails even before they reach your inbox.
- Enable two-factor authentication (2FA) – Wherever possible, try to use 2FA, specifically for email, and banking, as they add an extra layer of security.
- Use strong passwords – Always use strong passwords that have a combination of upper case, lower case, and special characters. Change passwords once a month and never reuse the same password for multiple accounts. You can also use a password manager to save and generate secure passwords.
- Report phishing attempts – If you receive a phishing email or discover a suspicious website you can report it to the relevant cybercrime department of your government or organization (such as the Anti-Phishing Working Group (APWG) or the Federal Trade Commission (FTC) in the US). You can also mark an email as ‘phishing’ through the options provided by your email service provider
- Update your browser – Don’t ignore browser updates as every release come with security patches and updates
- Don’t click on pop-ups – Don’t click on pop-ups as they are often linked to malware. They will try and trick you with a “Close” button, so always look for an “x” in one of the corners
How can Cyber Sierra help against phishing?
With Cyber Sierra’s employee security training feature, you can launch continuous phishing campaigns that simulate real-world cyber threats. This hands-on approach will enable your employees to recognize and respond to phishing attempts effectively.
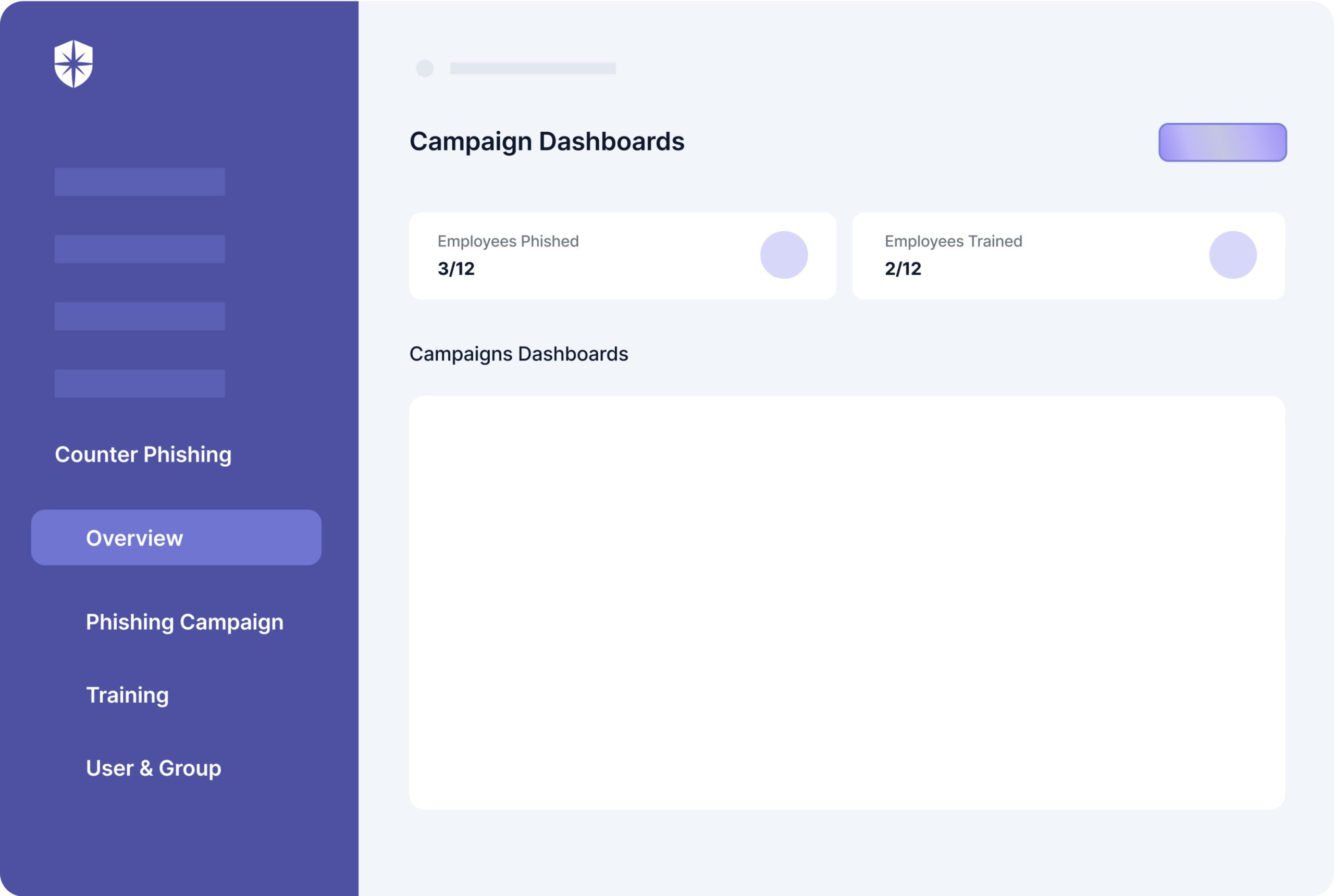

By creating a heightened sense of awareness, your workforce becomes more adept at identifying and mitigating potential risks, safeguarding your organization from external threats.
Don’t leave your security to chance. Book a demo with us to know how you can empower your employees.



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.