Comply With Australian CIRMP Rules





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
If you’re an Australian organization handling critical infrastructure assets, you have less than three months to be CIRMP (Critical Infrastructure Risk Management Program) compliant! All responsible entities must implement a risk management program as per CIRMP rules by 17 August 2023.
Here’s a quick lowdown on the CIRMP rules. Read on to know if you need to comply, and, if yes, what should you implement before the deadline to meet the core CIRMP requirements.
For the uninitiated, on 17 February 2023, the Australian Government introduced the CIRMP rule. Governed by the Security of Critical Infrastructure Act 2018 (SOCI Act), this is the latest rule introduced by the Australian government to safeguard the country against global cyber threats and uplift the core security practices of critical infrastructure (CI) assets.


What is CIRMP?
CIRMP stands for Critical Infrastructure Risk Management Program. It is a set of requirements that entities responsible for critical infrastructure assets (CIAs) must meet under the Security of Critical Infrastructure Rules 2023 in Australia.
The rule states that entities responsible for CIAs must implement a critical infrastructure risk management program by 17 August 2023.
What is material risk?
A material risk as per CIRMP is a risk that has a significant impact on the ability of a critical infrastructure asset to perform its critical functions. This could include risks that could lead to the impairment, stoppage, loss of access to, or interference with the asset.
Section 6 (a-e) of the Rules provides the parameters of a material risk.
The Australian Cyber Security Centre (ACSC) has provided some guidance on what constitutes a material risk in the context of the CIRMP. This guidance includes the following factors:
- The likelihood of the risk occurring.
- The impact of the risk if it does occur.
- The criticality of the asset to the economy or society.
- The cost of implementing measures to mitigate the risk.
The concept of material risk, however, isn’t absolute and each entity will need to assess the risks to its own assets on a case-by-case basis.
Here are some examples of material risks that could affect critical infrastructure assets:
A cyber attack that could disrupt or disable the asset’s IT systems.
A physical attack that could damage or destroy the asset.
A natural disaster that could cause the asset to be unavailable.
A human error that could lead to the asset being misused or damaged.
The CIRMP requires entities responsible for critical infrastructure assets to identify and assess the material risks to their assets. This assessment should be documented in the CIRMP and should be reviewed and updated on a regular basis. The entity should also implement measures to mitigate the material risks to its assets.
A ‘material risk’ to a critical infrastructure asset occurs when the risk has a
‘relevant impact’ on the asset. Section 6 (a-e) of the Rules provides the parameters
of a material risk.
These include the risk of impairment, stoppage, loss of access to or interference
with the asset.
What is a relevant impact?
A ‘relevant impact’ is an impact on the availability, integrity, and reliability of the
asset, and the impact on the confidentiality of information about the asset,
information stored in the asset if any, and, if the asset is computer data, the
computer data.
The relevant impact may be direct or indirect. It must be more serious than a
reduction in the quality of service being provided.
Why is the CIRMP Rule Important?
The CIRMP rule is important because it helps Australia’s critical infrastructure entities uplift their core security practices that relate to managing their critical infrastructure assets. It does so helping create a robust and proactive risk management program for organizations.
Market disruptions have increased the adoption of digital transformation among many businesses. While technologies such as automation, data processing, cloud, and AI improve productivity, security threats are also growing in intensity and complexity.
So, when your CI asset is disrupted by security threats, it can affect your business, the government, and the community. All of this can even damage the country’s economic growth.
Therefore, the only goal of CIRMP is to help Australian entities such as yours create a solid security program that will uplift the core security practices of your CI assets. When you have a strong security program as per the CIRMP rules, it’ll help you to,
- Safely provide services that the economy and community rely on
- Quickly bounce back from incidents that affect your critical assets
- Uphold your brand’s public perception and financial stability
To fully understand how the CIRMP rule came into place, you must know what the SOCI (Security of Critical Infrastructure) 2018 Act is about.
Compliance with CIRMP rules is not merely a matter of checking boxes; it is an ongoing process that requires organizations to fully implement and abide by the law’s principles. The CIRMP rules demand a comprehensive approach, with a particular emphasis on fortifying the cybersecurity of critical infrastructure.
This endeavour necessitates the collective effort of the entire vendor ecosystem, urging them to address any shortcomings and improve their practices.
Quick Rewind on the SOCI Act
The SOCI Act was amended in 2018 to improve the resilience of CI assets against security threats through carefully laid regulatory reforms and amendments. It was passed in two phases,
- The first phase in December 2021 – Security Legislation Amendment (Critical Infrastructure) Act
- The second phase in April 2022 – Security Legislation Amendment (Critical Infrastructure Protection) Act
Together these two amendments form a framework with the following features:
Government Direction and Intervention (in effect since Dec 2021)
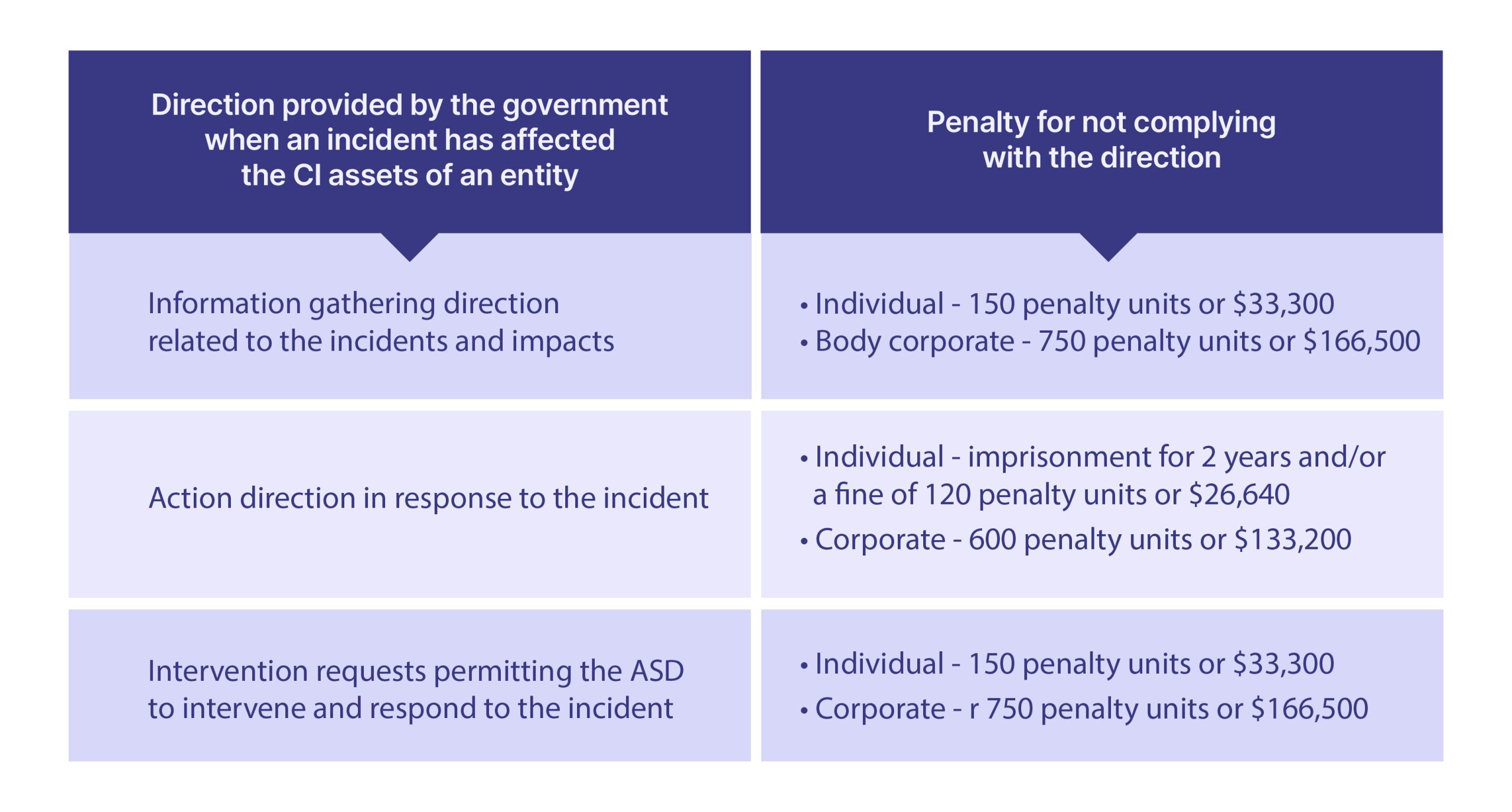

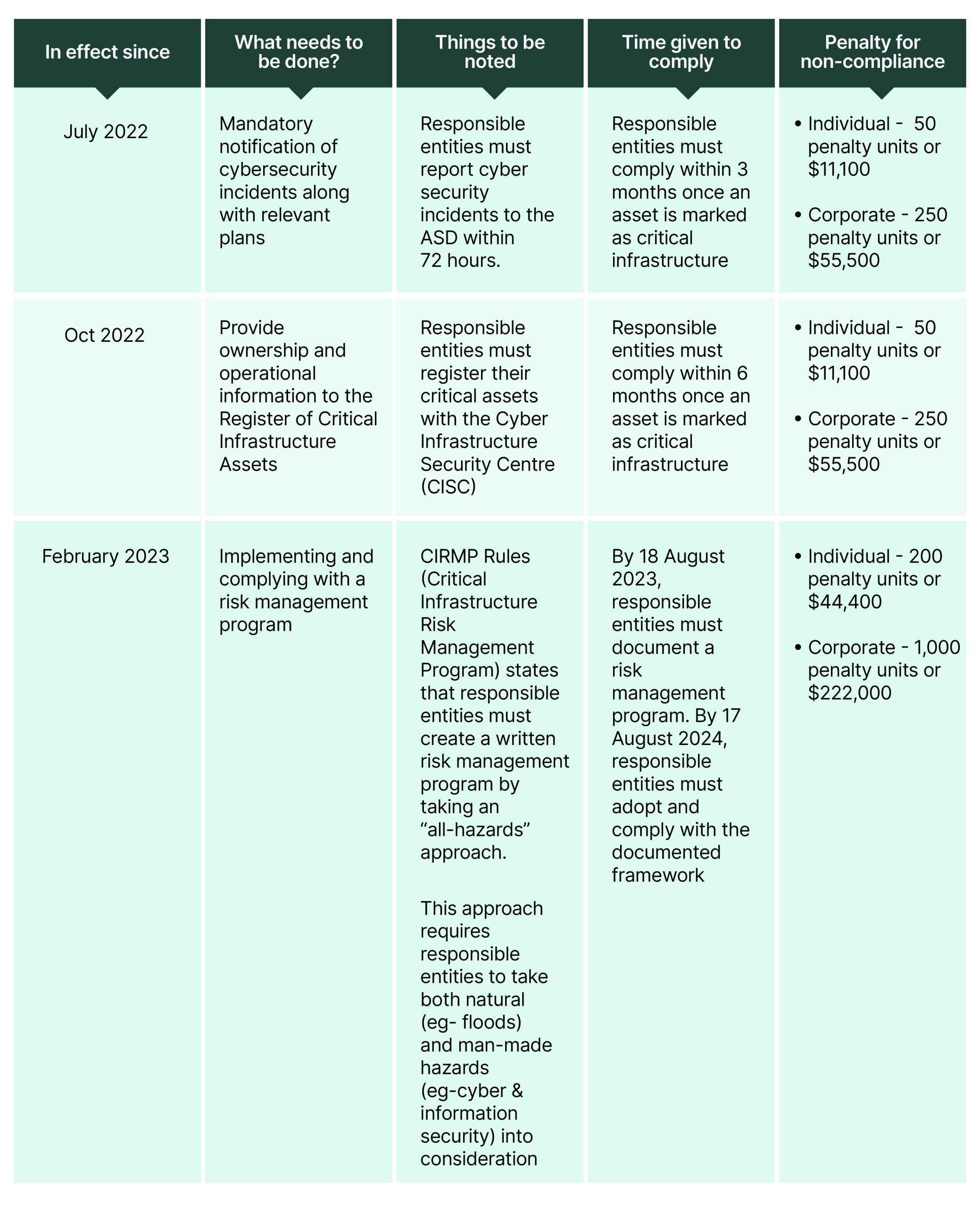
Positive Security Obligations – What Responsible Entities Need to Do to Ensure Compliance?

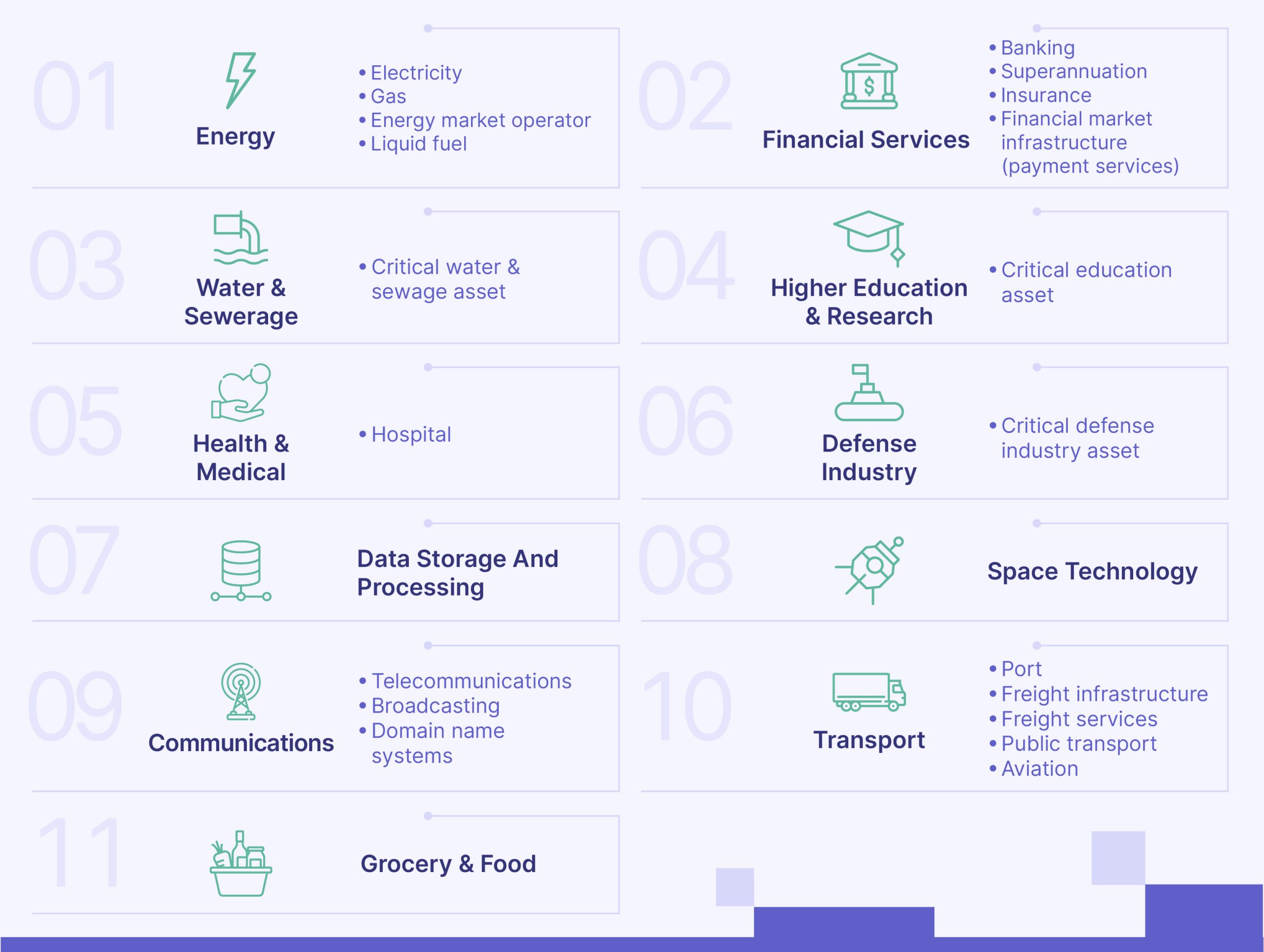
Who must comply with the CIRMP Rules?
The CIRMP rules apply to all Australian entities that own and manage critical infrastructure assets. The Australian government has outlined 11 critical infrastructure sectors and 22 categories of CI assets that must comply with CIRMP, including entities that manage CI assets. This includes critical financial services assets, critical energy assets, and others.
For detailed definitions of asset rules, click here.

How to comply with Australia’s CIRMP Rules?
Organizations can comply with Australia’s CIRMP rules by following these four steps:
Step 1 – Describe CIRMP requirements based on your CI assets
Step 2 – Define the four key hazard vectors of your CI assets
Step 3 – Submit annual reports to the Commonwealth regulator
Step 4 – Maintain, review, and update CIRMP
Organizations must develop, maintain and update their CIRMP. Here’s a detailed overview of how you can achieve each of these steps.
Step 1: Describe the CIRMP requirements
Here’s a basic list of what you need to complete to develop your CIRMP.
- Identify and document hazards, such as cyber & information security, personnel, supply chain, and physical security & natural hazards, that pose material risks to your CI assets. Next, determine the impact on the availability, dependability, and integrity of CI assets. Finally, develop strategies to minimize risks.
- Determine interdependency between the CI assets so mitigating circumstances can be broadened.
- Choose who will be responsible for creating, executing, reviewing, and updating your CIRMP
- Decide how CIRMP will be created, enforced, inspected, and updated.
- Outline the risk management frameworks and methodologies used.
Before you proceed further, here’s a quick look at the hazards that must be covered.
Step 2 – Define the four key hazard vectors of your CI assets
Here’s how you can identify hazards that pose material risks to your CI assets and mitigate their impact.
Cyber & information security hazards
This comprises risks to your digital systems, computers, datasets, and networks that can affect the working of your CI assets. You need to state the cyber and information security hazards that could impact your CI assets.
Some of the biggest cyber threats include,
- Phishing
- Malware
- Ransomware
- Credential harvesting
- Denial-of-service (DoS)
How to address them?
To minimize and eliminate these risks, as a responsible entity you must,
- Introduce risk management practices – Scan assets, catch vulnerabilities, access impacts, and employ relevant measures to monitor and fix the risks
- Add security measures across every product used in your business – Run scans, address vulnerabilities before deployment, and add security to every product development
- Invest in employee education – Run awareness & training programs related to cyber security risks, conduct counter-phishing campaigns, and help employees detect phishing emails
- Get insurance – Consider investing in the right insurance plan to protect your business and bypass expensive security breaches
- Third-Party Risk Management – Mitigate the risks by vendors (suppliers, third parties, or business partners) before and during your partnership by implementing appropriate Third-party risk management (TPRM) practices
Here are some of the cyber frameworks you can consider implementing. Make sure to follow one that is appropriate for your CI assets. Note that there are no restrictions related to frameworks; if these aren’t suitable, you can choose a different one.
- Australian Standard AS ISO.IEC 27001:2015
- Essential Eight Maturity Model by the Australian Signals Directorate – Level 1 maturity is required (click here to learn more about the levels)
- Framework for Improving Critical Infrastructure Cybersecurity by the US National Institute of Standards and Technology
- Cybersecurity Capability Maturity Model by US Department of Energy – Level 1 maturity is required
- The 2020-21 AESCSF Framework Core published by Australian Energy Market – Level 1 maturity is required
Personnel hazards
Personnel hazards cover workers and contractors who access sensitive information about your CI assets. You must, therefore, define activities such as proper onboarding, offboarding, background checks, and setting access controls for personnel.
How to address them?
- Identify critical workers who access, control, and manage critical assets. And closely monitor them
- Set authorized access controls for both physical and digital assets
- Use services such as AusCheck or others to do a proper background check of critical workers
- Conduct regular cyber security training for critical workers
Supply chain hazards
Unauthorized access to the supply chain, upsetting the supply chain assets, and vendor risks are some of the hazards you must consider here.
You can consider measures to establish and maintain a system that prevents unauthorized access to the supply chain, misuse of given access, upsetting the supply chain assets, and bypassing threats in the supply chain caused by products, services, and personnel.
How to address them?
- Identify your supply chain process. List down who your vendors are, the countries they are from, and who the owners of your vendors are, and outline any third-party dependencies
- Include proper cyber security in all of your supply chain agreements
- Identify supply chain bottlenecks to diversify vendors
- Implement physical security & make allowance for natural hazards
Physical and natural hazards
You must also address illegal physical access and natural hazards to critical components. So, don’t forget to make a note of the risks of such occurrences alongside the steps to mitigate their impact.
How to address them?
- Identify the critical physical components and their security hazards. Outline all the natural hazards, such as earthquakes, tsunamis, and pandemics, that could affect your critical assets. This must also include biological hazards.
- Secure control systems through onsite measures and access controls with the use of HVAC, cameras, and fire alarm panels
- Create security drills to build infrastructure resilience
- Develop and maintain a bushfire survival plan
- Enforce physical access controls such as biometrics
- Install CCTV sensors to help your security staff better monitor things
Step 3 – Submit annual reports to the Commonwealth regulator
You need to submit your annual CIRMP reports to the applicable Commonwealth regulator by the end of the Australian financial year (28th September). This way, the Cyber Infrastructure Security Centre (CISC) and other related regulators can check if the program remains up-to-date. Besides, these entities can further advise you on the measures to strengthen the security of your CI assets.
Step 4 – Maintain, review, and update CIRMP
The SOCI also requires organizations to maintain the CIRMP status. You can accomplish by:
- Comply – Comply with the CIRMP rules
- Review – Maintain a process to review CIRMP every 12 months
- Update – Ensure the program is up to date
How to Strengthen Your Compliance & Security Requirements As Per CIRMP Rules?
Compliance with CIRMP rules is not merely a matter of checking boxes; it is an ongoing process that requires organizations to fully implement and abide by the law’s principles. The CIRMP rules demand a comprehensive approach, with a particular emphasis on fortifying the cybersecurity of critical infrastructure.
This endeavour necessitates the collective effort of the entire vendor ecosystem, urging them to address any shortcomings and improve their practices.
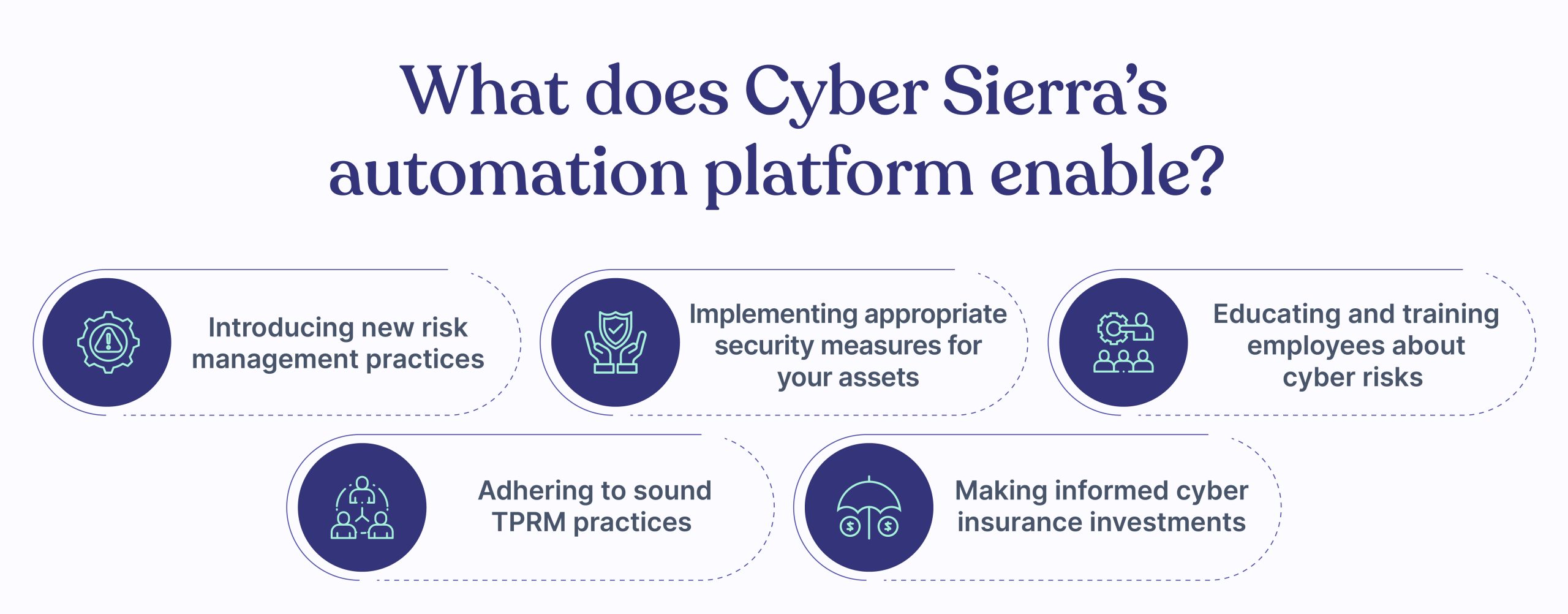
Cyber Sierra’s ThirdParty Risk Management module is custom-built to help organizations up their security game in accordance with the CIRMP rules. The automation platform is equipped to assist you in various areas, including developing new risk management practices, implementing appropriate security measures for your assets, educating your employees about cyber risks, adhering to sound TPRM practices, and making informed cyber insurance investments.
Our specialized continuous controls monitoring is designed to ensure you maintain complete control and serves as effective “reasonable security measures” in the event of a breach, preventing hefty penalties. Moreover, continuous control monitoring surpasses the limited sample-based testing of controls provided by audit firms; it is comprehensive, ongoing, and supported by data.

Schedule a free demo with our cybersecurity experts to learn how to enhance your risk management program in accordance with the Australian CIRMP rules.
FAQs
Which are the sectors that come under Australia’s CIRMP obligation?
The following sectors are subject to the Australian CIRMP obligations:
- Energy
- Water and Sewerage
- Data Storage
- Financial Services
- Transportation
- Food and Grocery
- Healthcare and Medical
- Communications
What does the CIRMP require of organizations?
The CIRMP requires organizations to address four main areas: cyber and information security hazards, personnel hazards, supply chain hazards, and physical security and natural hazards.
In each of these areas, organizations must identify risks that could affect their assets, minimize or eliminate those risks, and mitigate the impact of any hazards on their assets. Specifically, in the cyber and information security domain, organizations need to comply with established cybersecurity standards and frameworks.
- Australian Standard AS ISO.IEC 27001:2015
- Essential Eight Maturity Model by the Australian Signals Directorate – Level 1 maturity is required (click here to learn more about the levels)
- Framework for Improving Critical Infrastructure Cybersecurity by the US National Institute of Standards and Technology
- Cybersecurity Capability Maturity Model by US Department of Energy – Level 1 maturity is required
- The 2020-21 AESCSF Framework Core published by Australian Energy Market – Level 1 maturity is required
- A framework equivalent to any of the above
The deadline for implementing a CIRMP and complying with the controls is August 17, 2023, with full compliance required by August 17, 2024.
What is the penalty for failing to comply with CIRMP?
If a company doesn’t have or follow a CIRMP, it can be fined 1,000 penalty units or $275,000 per day. This applies to not meeting the obligations of the CIRMP, except for the annual reporting requirement, which carries a fine of 750 penalty units or $206,250 per day if not met. These penalties also apply if a company fails to fully implement their CIRMP.
Cyber Sierra’s continuous control monitoring offers ‘reasonable security measures’ in the event of a breach, preventing companies from paying hefty penalties for noncompliance.
Disclaimer – Detailed regarding the rules mentioned in this blog were sourced from CIRMP rules and SOCI act shared by the Australian Government. The contents of this blog are not a substitute for legal advice. You must always get professional advice or help for matters your organization may have.
Find out how we can assist you in completing your compliance journey.