A Guide to Cyber Hygiene Best Practices



Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Picture this scenario: Your organization’s network has fallen victim to a breach, resulting in the compromise of your valuable customer information. As if that wasn’t distressing enough, you suddenly uncover that your personal email account has been unlawfully accessed. In a single moment, both your professional aspirations and personal endeavors are thrown into disarray.
How would you respond in such a situation? It’s probable that your reaction wouldn’t be favorable. When a hacker manages to breach one device, they gain potential access to all aspects of your online presence. That is precisely why practicing good cybersecurity hygiene is crucial for both individuals and businesses.
In this article, we will delve into the significance of cyber hygiene and its role in enhancing your online security. We will explore various measures and practices that can be adopted to bolster your defenses against cyber threats.
What is Cyber Hygiene?
Cyber hygiene is a set of best practices that individuals and organizations can embrace to safeguard themselves against cyber threats. Its fundamental objective is to shield user accounts, data, and systems from potential attacks that may jeopardize their security. By adhering to cyber hygiene principles, individuals and organizations can fortify their defenses and minimize the risks associated with online vulnerabilities.
This includes:
- Regularly updating software and operating systems,
- Using strong and unique passwords,
- Avoiding suspicious links and emails, and much more.
What Are the Components of Cyber Hygiene?
Cyber hygiene encompasses a range of practices and habits that effectively safeguard users against threats like phishing and malware. The following components are integral to maintaining cyber hygiene:
- Monitoring systems and databases
- Managing user access
- Protecting sensitive data
Let’s look at these in detail.

1. Monitoring systems and databases
Monitoring systems and databases regularly for unusual activity or access can help identify potential vulnerabilities or threats. This includes reviewing logs and reports as well as analyzing any unusual activity.
2. Managing user access
An organization must control user access to sensitive data to ensure that only authorized individuals can access it.
This includes implementing strong authentication measures such as two-factor or multi-factor authentication and regularly reviewing and updating access permissions so that the organization can better manage user access.
3. Protecting sensitive data
Organizations should protect sensitive data by implementing appropriate technical measures, such as encryption and access controls. This includes protecting data at rest and in transit through the use of encryption technology. It is also important that this data be regularly backed up in case a cyber attack causes loss or damage.
This will allow the organization to restore its data and continue operations without significant disruption.
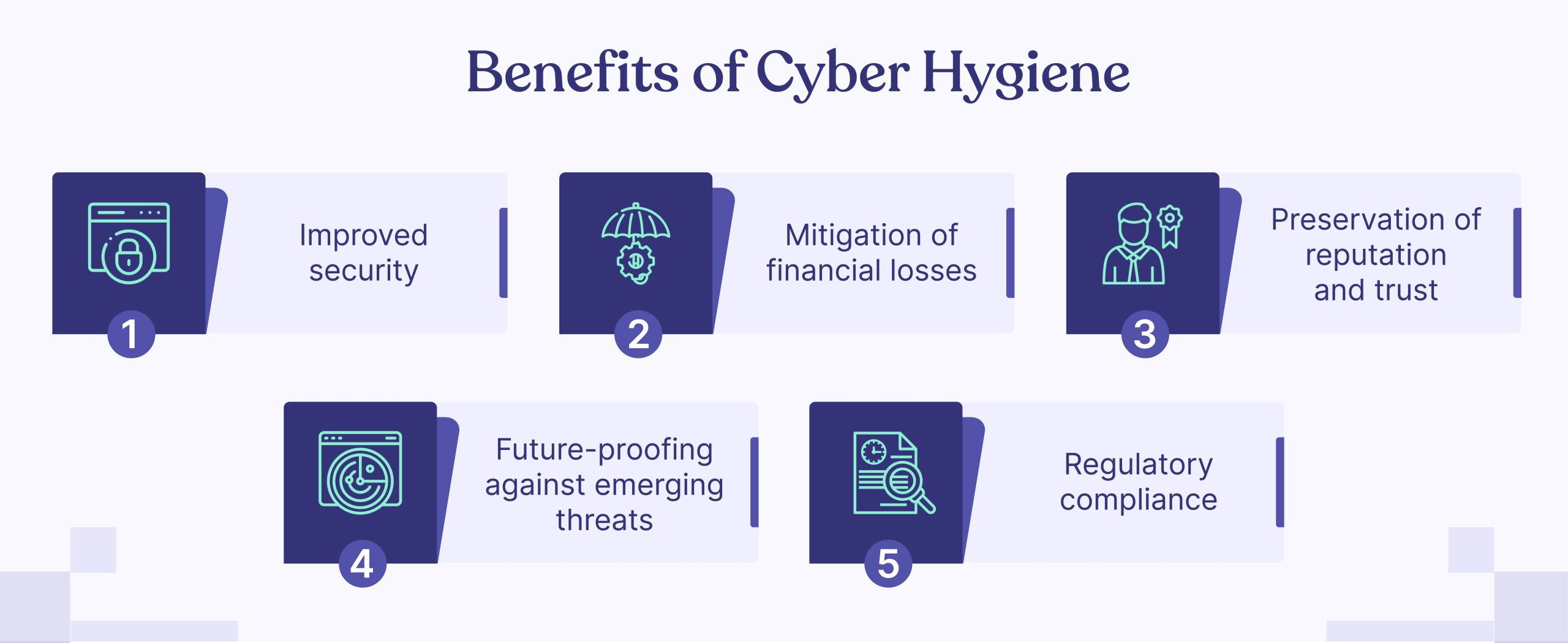
Benefits of Cyber Hygiene
The benefits of cyber hygiene are numerous and extend to both individuals and organizations. Here are some of its key benefits:
- Improved security
- Mitigation of financial losses
- Preservation of reputation and trust
- Future-proofing against emerging threats
- Regulatory compliance
Let’s look at them one by one.

1. Improved security
One of the most essential benefits of cyber hygiene is improved security. A well-executed cyber hygiene program will help organizations
- Identify and address security gaps,
- Reduce the attack and
- Heighten the difficulty for attackers to compromise their systems.
This is because many of the best practices in cyber hygiene or design reduce risk by making an organization’s infrastructure more secure overall.
For example, creating a patch management system that updates software to prevent vulnerabilities can help reduce the number of exploitable flaws in your systems.
2. Mitigation of Financial Losses
Cybersecurity incidents can result in substantial financial losses for individuals and organizations. In fact, on average, cyber crimes result in losses that amount to 2.5% of the global GDP.
That’s why it’s essential to implement practices like,
- Changing passwords,
- Updating software, and
- Enforcing policies that require users to practice good password hygiene
All this can help reduce the risk of data breaches, cyber-attacks and other security incidents.
3. Preservation of Reputation and Trust
A cyber attack can have a significant impact on an organization’s reputation and trust. A breach of privacy or the leaking of sensitive data can result in a loss of confidence from customers and a drop in sales.
Implementing best practices like encrypting data at rest, restricting access to confidential information, and having strong password policies can help prevent breaches that could result in loss of reputation or trust.
4. Future-Proofing Against Emerging Threats
Cyber threats are continually evolving, with new types of attacks and vulnerabilities emerging regularly.
A robust cyber hygiene program helps organizations stay ahead of these threats by regularly evaluating and updating their security measures, ensuring they are prepared to defend against new and emerging risks.
This proactive approach to cybersecurity can save organizations time, money, and resources in the long run, as they will be better equipped to prevent or mitigate the impact of future attacks.
5. Regulatory Compliance
The regulatory landscape surrounding data protection continues to evolve, with stringent laws and regulations being enforced worldwide. This is especially true in the financial services industry, where data protection is a top priority for compliance.
Organizations that do not comply with these regulations can face significant penalties and reputational damage, which can result in lost business opportunities.
A robust cyber hygiene program helps organizations stay ahead of these laws and regulations by regularly evaluating their security measures to ensure they are compliant with new laws and standards as they emerge. This proactive approach to cybersecurity can save organizations time, money, and resources in the long run, as they will be better prepared when new regulations come into effect.
Best Practices of Cyber Hygiene for Businesses
The best practices of cyber hygiene for businesses include:
- Regularly updating software and operating systems
- Implementing strong password policies
- Educating employees about cybersecurity risks
- Establishing a comprehensive cybersecurity policy
- Conducting regular security audits
- Implementing a Cloud Access Security Broker (CASB)
- Creating an incident response plan
- Ensuring endpoint protection
Let’s look at these best practices in more detail.

1. Regularly updating software and operating systems
According to a study by Ponemon Institute, 60% of data breaches were linked to unpatched vulnerabilities.
This is because many organizations either do not regularly update the software and operating systems in their networks or do not have a comprehensive patching strategy. It’s important that you take care of this security issue by implementing regular updates for all your devices.
When a new software package is released, it usually includes security patches that help protect against known vulnerabilities.
If your organization isn’t automatically updating its software, you risk exposing your network to cyber criminals who could exploit these vulnerabilities.
2. Implementing strong password policies
Businesses should enforce strong password policies, requiring users to create unique, complex passwords that are changed regularly, as over 80% of hacking-related breaches happened due to weak/stolen passwords.
Here are some best practices for creating strong password policies:
- Passwords should be at least 10 characters and include a mix of lowercase and uppercase letters, numbers, and symbols.
- Don’t use words that can be easily guessed (e.g., your name, username, etc.) or have been used in previous hacks of other companies databases.
- Use different passwords for each account—don’t reuse the same password for multiple accounts.
Additionally, multi-factor authentication (MFA) can provide an extra layer of security for sensitive accounts and systems.
3. Educating employees about cybersecurity risks
Employees should be trained to recognize and avoid common cybersecurity threats, such as phishing emails, suspicious links, and social engineering attacks.
For example, employees should be taught why they should avoid clicking on links in emails that erroneously appear to come from their company or its vendors. And how they should check the sender’s email address and verify if it matches those listed on the company’s website before opening any attachments or clicking on links in that email.
Businesses can make this easier by implementing security awareness training programs that provide the tools and knowledge necessary to help employees stay safe online.
Cyber Sierra has a comprehensive employee security training module that includes multiple counter phishing campaigns that simulate phishing attempts. Talk to us to know more about our employee security training program.
4. Establishing a comprehensive cybersecurity policy
A clear, comprehensive cybersecurity policy should outline the roles and responsibilities of employees and the procedures and protocols to follow in case of a security incident. This policy should be regularly reviewed and updated to stay current with emerging threats and industry best practices.
This will ensure your organization has the resource and knowledge to identify cyberattacks, and the best practices to respond to security incidents.
5. Conducting regular security audits
Regular security audits can help businesses identify potential vulnerabilities and areas for improvement in their cybersecurity posture. This will allow you to identify weaknesses and take proactive measures to fix them.
Security audits can be conducted by people who are experts in the subject of security and how to use it properly. The results will help businesses improve their cybersecurity practices, thereby making them less susceptible to cyberattacks.
Cyber Sierra’s threat intelligence feature can help you run vulnerability scans and conduct penetration testing periodically. It also has a continuous control monitoring feature that flags security gaps and makes suggestions to remediate them as well.
6. Implementing a Cloud Access Security Broker (CASB)
A cloud access security broker (CASB) is a software solution that can be deployed on-premise or in the cloud. It offers visibility and control over how employees use SaaS applications, including Office 365. It also provides security controls for these applications such as data encryption, malware protection, user authentication, and more.
A CASB can also help enforce your company’s security policies. It provides better visibility and control over the data in cloud-based applications by authenticating, encrypting, detecting loss of sensitive information (e.g., PII or PHI) and preventing malware infections within those apps.
7. Creating an Incident Response Plan
There have been many high-profile cyber attacks on corporations in recent years, such as the Colonial Pipeline Ransomware Attack (2021), T-Mobile Cyber Attack (2021), and SolarWinds Hack(2020). So, while you do everything to build your cyber security moat to protect your business, it is equally important to develop and implement incident response plans to deal with cyber attacks and incidents.
A solid incident response plan, therefore, is a must for any organization. This plan should include steps to take if an incident occurs, who’s responsible for certain tasks and how long it should take to complete each step.
8. Ensuring Endpoint Protection
Endpoint protection is a very important part of your overall security strategy, but many organizations fail to implement it properly. You must know what’s happening on each endpoint, who has access and which applications are installed.
Most businesses provide their employees with Internet-connected devices, such as laptops and mobile phones, so they can access the corporate network. While it may be tempting to overlook endpoint devices, businesses should ensure that these computers have appropriate protections in place—such as antivirus software, firewalls, and encryption—to keep data secure.
Best Practices of Cyber Hygiene for Individuals
For individuals, there are several steps you can take to help protect yourself from cyberattacks. Here are some tips:
- Use strong, unique passwords
- Enable multi-factor authentication (MFA)
- Keep your software and devices up-to-date
- Be cautious with public Wi-Fi
- Be vigilant against phishing and social engineering attacks
Let’s look at each of these in more detail.

1. Use strong, unique passwords
Create strong, unique passwords for your online accounts, and change them regularly. A Verizon study found that 81% of hacking-related breaches are caused by stolen or weak passwords.
Avoid using easily guessable information, such as your name, birthdate, or common words. Consider using a password manager to help you generate and store secure passwords.
2. Enable multi-factor authentication (MFA)
Whenever possible, enable multi-factor authentication (MFA) for your online accounts. MFA adds an extra layer of security by requiring additional verification, such as a code sent to your phone, fingerprint, or facial recognition.
This extra step helps prevent unauthorized access to your account.
3. Keep your software and devices up-to-date
Regularly update your software, operating systems, and devices to help protect against known vulnerabilities. Enable automatic updates to ensure your devices always run the latest security patches.
It is also essential to stay on top of security updates for all your software, including operating systems and applications.
4. Be cautious with public Wi-Fi
Avoid using public Wi-Fi networks for sensitive tasks like online banking or accessing sensitive data. If you must use public Wi-Fi, use a virtual private network (VPN) to encrypt your connection and protect your data from potential eavesdroppers.
5. Be vigilant against phishing and social engineering attacks
Learn to recognize and avoid phishing emails, suspicious links, and social engineering attacks. Do not click on links or download attachments from unknown sources, and always verify the legitimacy of a website before entering your login credentials or personal information.
Wrapping Up
In conclusion, the best way to keep your data safe is to practice good cybersecurity hygiene and be aware of the potential threats to data security. It is important to remain vigilant against cyberattacks and data breaches, as the consequences of losing your information could be devastating. Even if you do not feel like a “high-value target” for hackers, it is still important to take precautions to protect yourself from cybercriminals.
However, cyber hygiene is not a one-time effort but rather an ongoing process that requires constant vigilance and adaptation to the ever-changing landscape of cyber threats. Follow these steps, and you’ll be well on your way to protecting yourself from hackers and other bad actors.
Frequently Asked Questions
1. What is the importance of cyber hygiene?
Cyber hygiene is essential for protecting personal and organizational information from cyber threats. Implementing and maintaining a set of best practices can help individuals and organizations reduce their risk of cyber attacks, protect sensitive data, and preserve their reputation with customers/stakeholders.
2. How can businesses improve their cyber hygiene?
Businesses can improve their cyber hygiene by implementing best practices to protect sensitive data and reduce the risk of a cyber attack. These include:
- Regularly updating software, including programs for antivirus protection, firewalls, and operating systems.
- Locking down user accounts with strong passwords (at least eight characters with a combination of letters and numbers)
- Educating employees about cybersecurity risks and how to avoid them
- Regularly testing their networks for vulnerabilities (using a third party if necessary) and patching any security holes that are discovered.
3. What can individuals do to maintain good cyber hygiene?
To maintain good cyber hygiene, individuals can undertake several proactive measures to protect their online security. Here are some essential practices:
Strong and unique passwords: Create strong, complex passwords that are unique for each online account. Avoid using easily guessable information and consider using a reliable password manager to securely store and manage passwords.
Two-factor authentication (2FA): Enable 2FA whenever possible to add an extra layer of security. This requires a second verification step, such as a unique code sent to a mobile device, in addition to a password.
Regular software updates: Keep all devices and software up to date with the latest security patches. Updates often address vulnerabilities that hackers may exploit.
Awareness of phishing attempts: Be cautious of suspicious emails, messages, or links. Avoid clicking on unfamiliar or unsolicited attachments or providing personal information unless you are certain of the source’s legitimacy.
Secure Wi-Fi and network connections: Use encrypted Wi-Fi networks and avoid connecting to public or unsecured networks when handling sensitive information. Ensure your home network has a strong password and a secure encryption protocol.
Regular backups: Back up important files and data regularly to an external hard drive, cloud storage, or both. This protects against data loss in case of ransomware attacks or device failure.
Social media privacy settings: Review and adjust privacy settings on social media platforms to control the visibility of personal information and restrict access to your profile.
Safe browsing habits: Exercise caution when visiting websites and downloading files. Stick to reputable websites and avoid clicking on suspicious links or downloading files from untrusted sources.
Educate yourself: Stay informed about the latest cyber threats and security practices. Attend online security awareness training, read reliable sources, and follow trusted cybersecurity experts for guidance.
Find out how we can assist you in completing your compliance journey.