Cybersecurity Insurance: A CTO’s Guide






Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
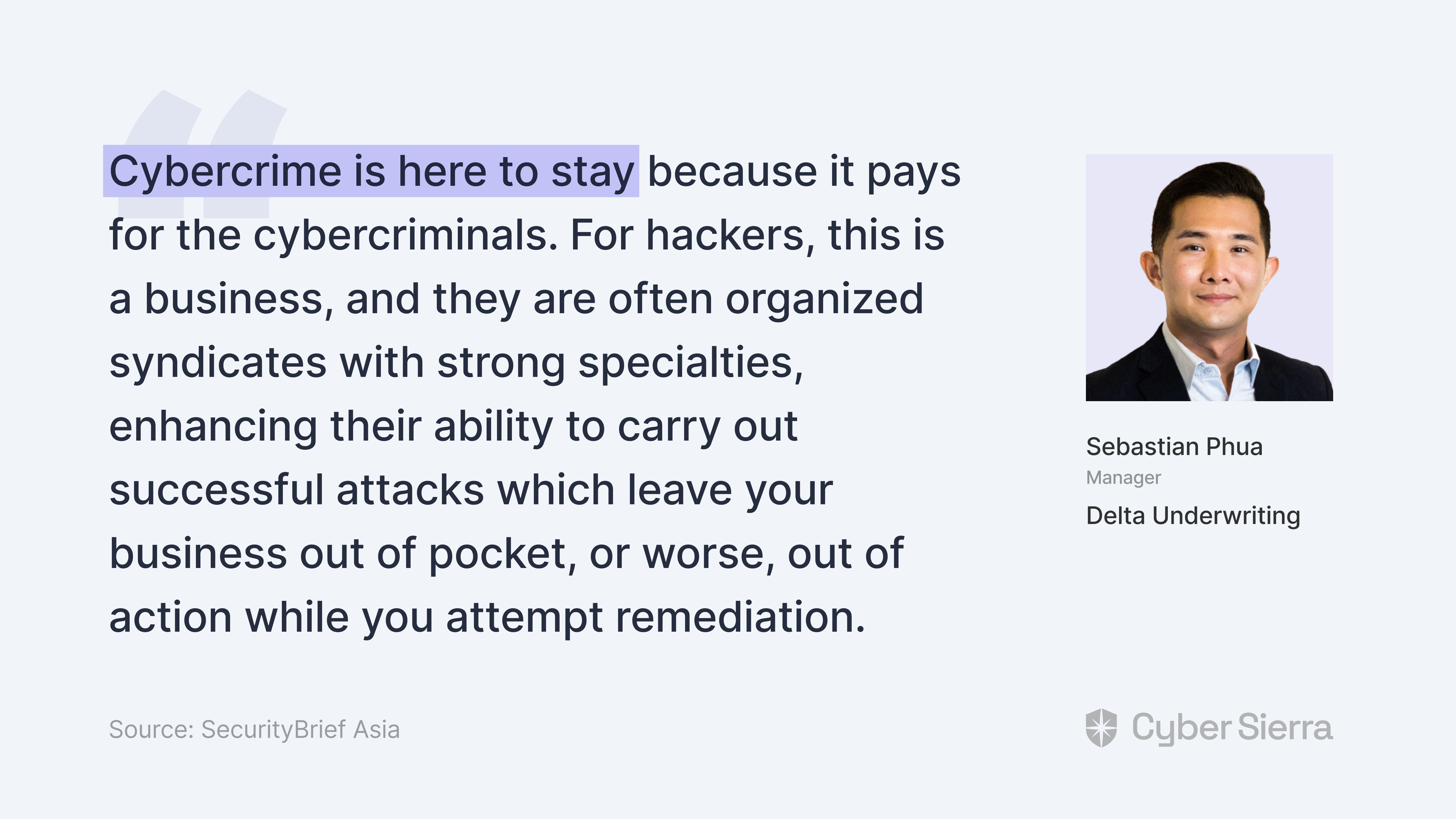
Cybercrime across Asia is ‘here to stay.’
Sebastian Phua, Manager at Delta Underwriting, also observed this in a report by SecurityBrief Asia:

And the stats support it, too.
In India, for instance, recorded cybersecurity incidents spiked from 3,94,499 in 2019 to a whopping 14,02,809 in 2021. This scary 3-fold increase isn’t far from the dire situation in Singapore.
In their case, 2021 saw a 145% YoY cybersecurity incident spike, with about two million cyberattacks recorded in Q2 2022 alone:


Due to this ever-expanding threat landscape:
- Insurance companies are more critical of who gets insured,
- The onus is on you, the CTO or the security head, to do all that’s needed to protect your company from future attacks by getting insured.
Both scenarios affirm that…
Yes, Cybersecurity Insurance is a Necessity
…a necessity getting harder to access.
It’s no longer ‘if’ a cyberattack could happen but ‘when.’ This has increased demand for coverage. Higher demand for cyber insurance means premiums will remain high. However, being able to afford a high premium isn’t automatic access to getting coverage.
Insurers are scrutinizing companies more. More documentation and real-time insight into cybersecurity postures are required. Now, access to cyber coverage is more likely if your company already has a mature cybersecurity system for detecting and assessing risks.
Says Sue Poremba of SecurityIntelligence:


In line with Sue’s words, to meet requirements and access coverage without sweating over it, IT execs in Asia must be proactive by:
- Knowing what cyber coverages to prioritize
- Implementing risk-assessing systems to meet requirements
- Streamlining the process of applying for coverage.
We’ll discuss all three today.
As we proceed, you’ll also see how Cyber Sierra’s interoperable platform eases access to cyber insurance in India and Singapore:
Cyber Insurance Coverages Executives Should Prioritize
According to Mark Rosanes of InsuranceBusiness:


One way to navigate this hurdle is to examine where companies in the IT sector have made more insurance claims recently. With this knowledge, you can determine where to channel cybersecurity resources. And more importantly, what insurance coverages to buy.
Good thing Astra’s cyber insurance statistics report revealed major reasons for insurance claims in the IT and communications sector:
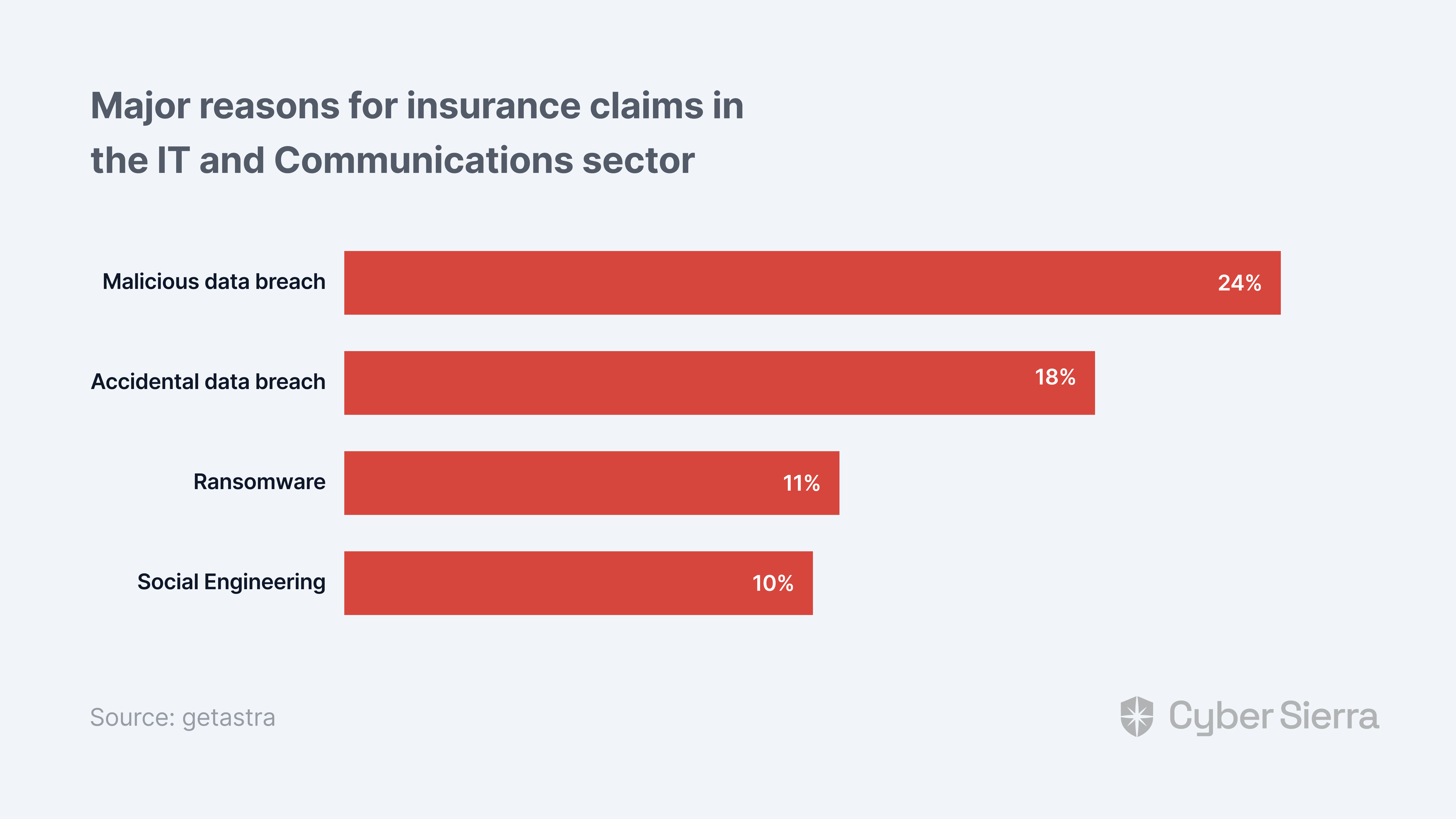

Below is how to increase your organization’s chances of getting cyber coverage against these threats.
Coverage for Malicious Data Breach (Cyber Insurance)
Cybercriminals are striking victims in more sophisticated ways.
They are devising new ways to hack tech infrastructures or constantly hunting for vulnerabilities in cloud or network systems they can latch onto. And because you can’t be sure where they’ll find a loophole, cyber insurance coverage is necessary. It insures your company from losses arising from external malicious data breaches.
Mr. Eric Cho, a Cyber Underwriter at Munich Re, highlighted a crucial requirement for securing this coverage:


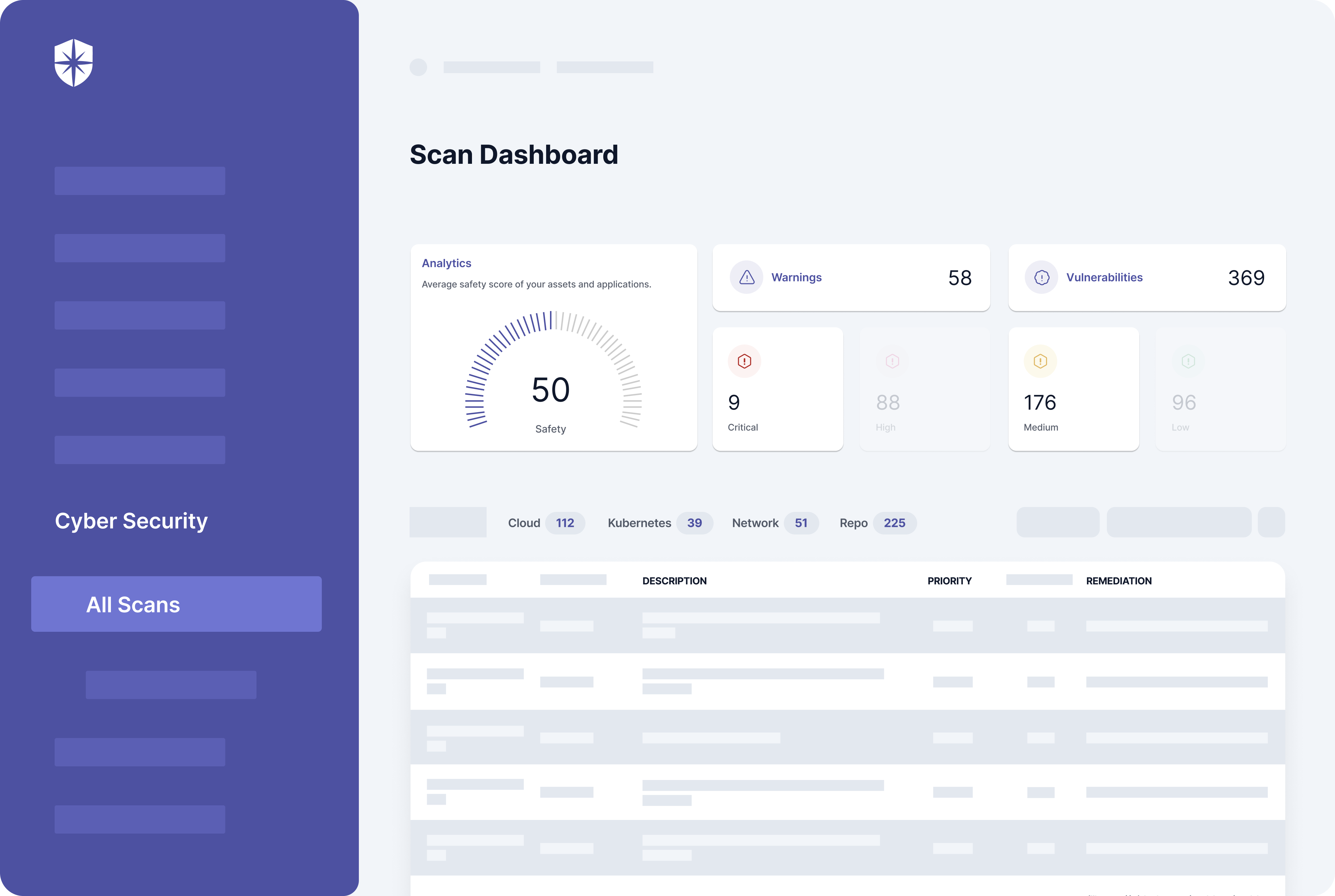
Put another way, having a platform for assessing your cybersecurity posture is a necessity for this insurance coverage. An excellent one will continuously scan data from your cloud, Kubernetes, network, repository systems, giving you (and insurers) a view of your company’s cyber posture.
That’s one capability Cyber Sierra has out of the box:

Accidental Data Breach Coverage (Errors & Omissions Insurance)
For its 2021 study, NetDiligence analyzed over 4,600 insurance claims between 2016 and 2020. Their research found that three out of the top five insurance claims by causes of loss were:
- Business email compromise,
- Staff mistakes, and
- Phishing.
As the study also noted, all three lead to data breaches usually taken to be ‘accidents’ if employees mishandle privileged company data. Errors & Omissions insurance covers losses from such accidents. Coverage takes care of the costs such as fines, legal fees, forensic research, and others.
But to access it, ongoing security awareness training is a requirement sought by insurers. Errors & Omissions Underwriters at Woodruff Sawyer, Stephen Quintana and Aaron Casey, stressed this in a recent report.
They wrote:


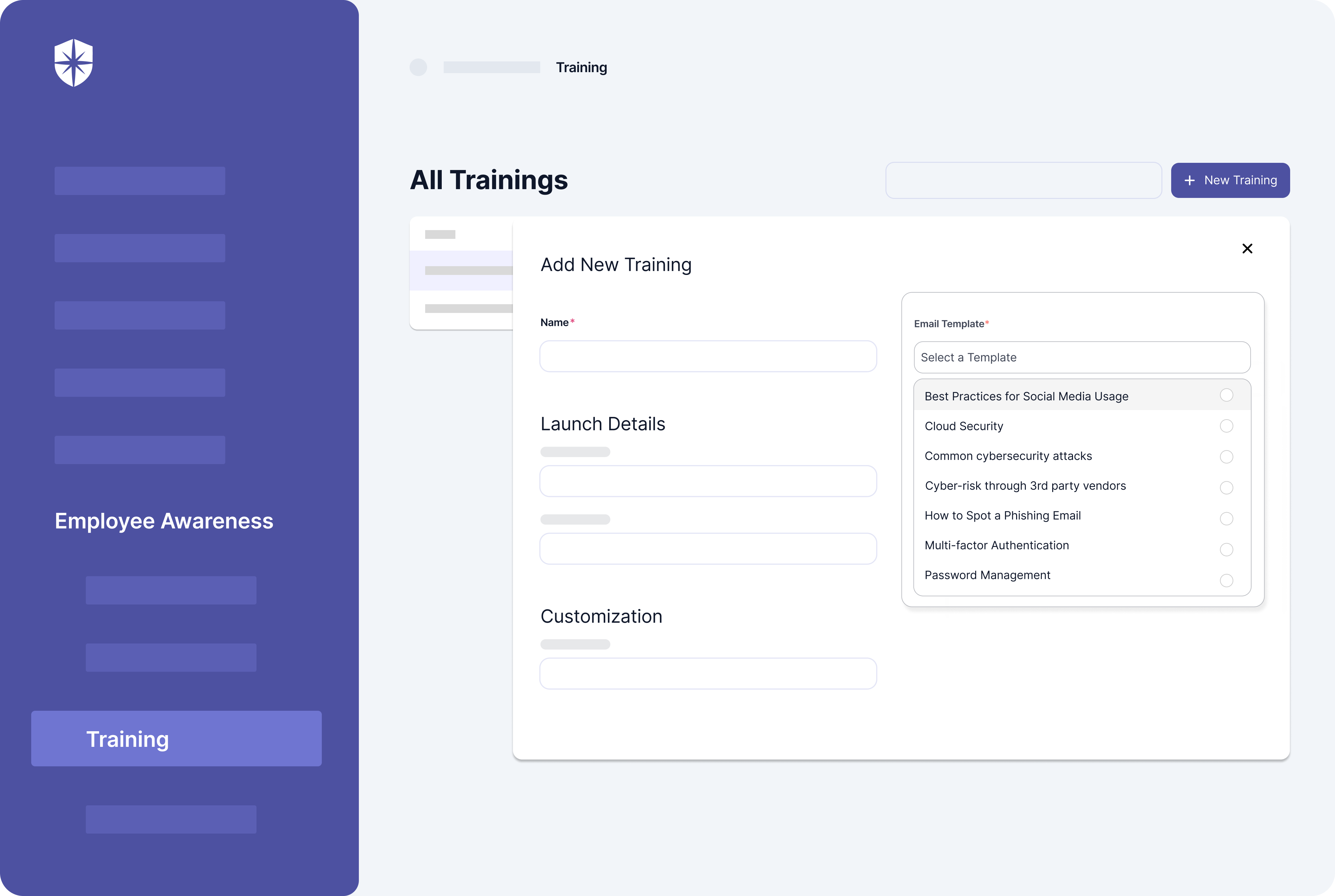
In other words, ongoing awareness training to educate employees on ways to avoid omissions that lead to accidental data breaches is a prerequisite.
This includes:
- Best ways to use social media
- Cyber risks through 3rd-party vendors
- How to spot phishing emails
- Multi-factor authentication
- Safe browsing habits
- Sensitive data handling
- Common cybersecurity attacks
- And others.
Your team can do all these with Cyber Sierra:

Business Interruption Coverage (Ransomware Insurance)
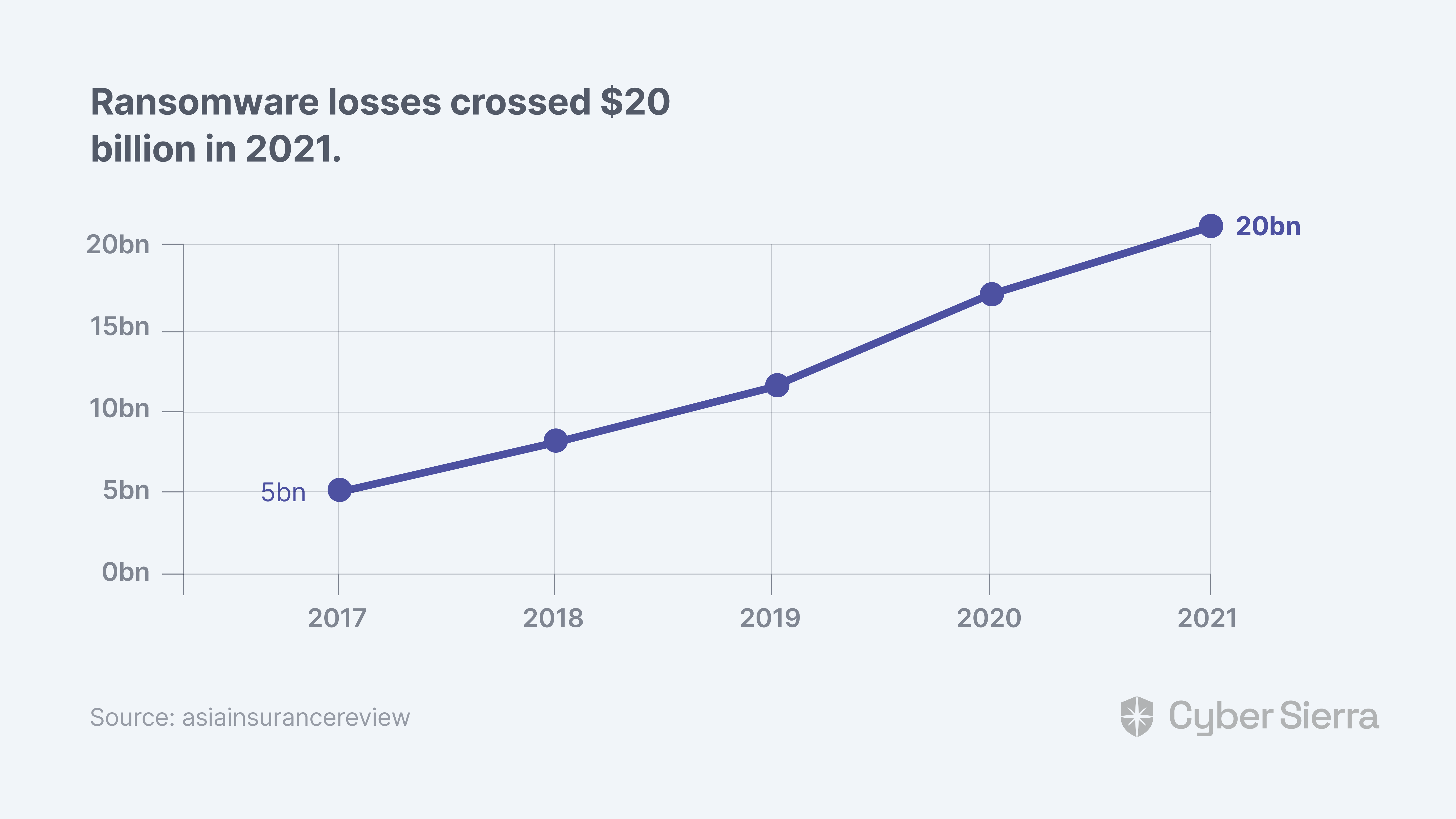
The Asia Pacific region accounted for over 7% of reported ransomware incidents in 2020, per a report by the Asia Insurance Review. That same year, global losses from ransomware hit US$17 billion.
One year later, in 2021, it crossed US$20 billion:

According to Andreas Schmitt, Head of Cyber Asia at Munich Re, insurance for this ever-growing threat area is crucial because:
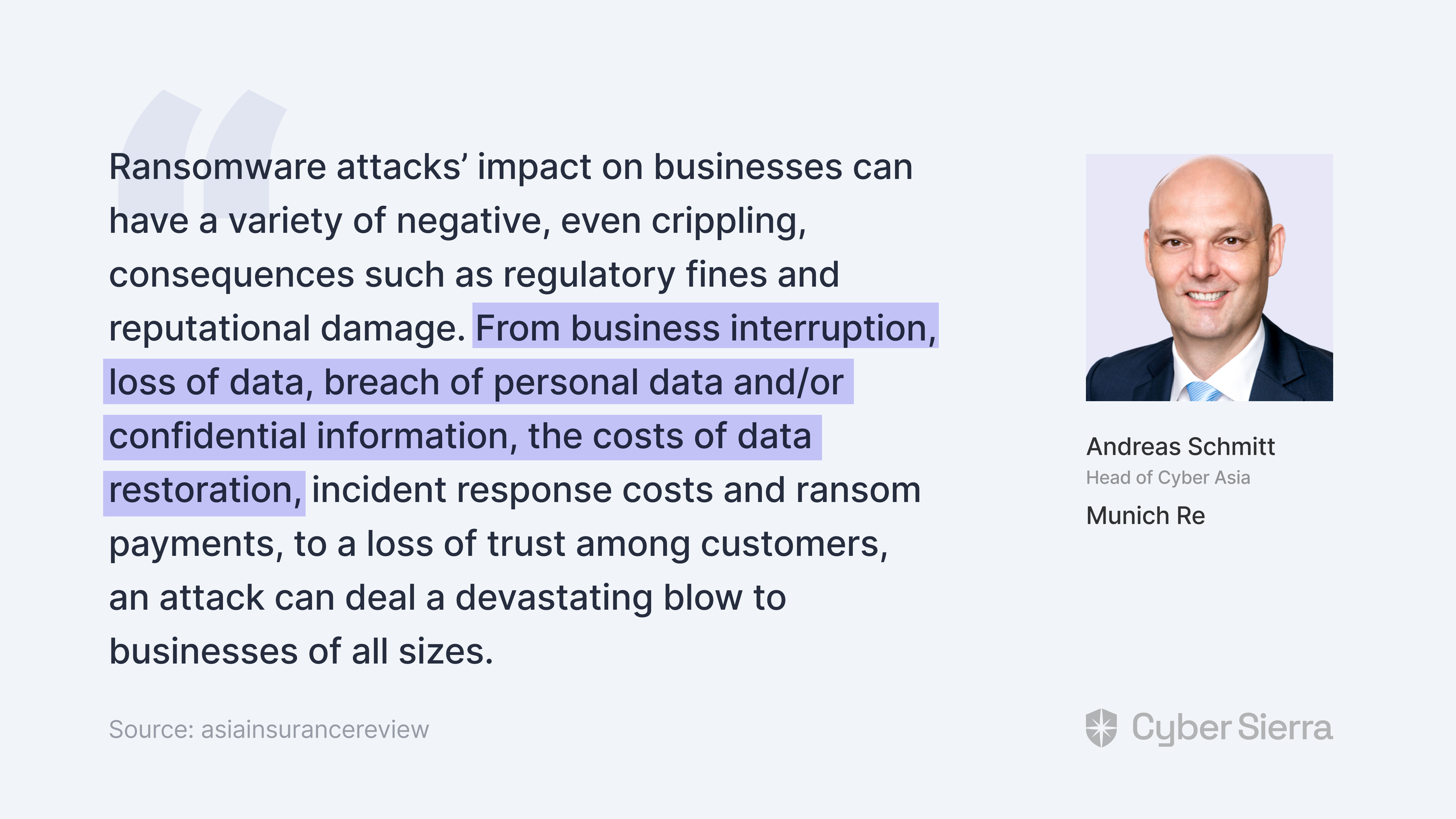

Ransomware coverage reduces the costs of these business interruptions. Mind you, ransomware attacks can happen irrespective of how threat actors access and lock you out of your company’s data.
So to meet policy requirements, an excellent starting point is to take a holistic approach to securing your organization’s data. Instead of stitching a slew of point cybersecurity tools that don’t work together, opt for an interoperable cyber solution suite that works well together.
And that’s where Cyber Sierra comes in:
Social Engineering Coverage (Professional Liability Insurance)
Social engineering has grown to become a top cause of insurance claims for companies in the IT and communications sector. According to the insurer, Chubb, an insurance policy against social engineering attacks will, among other things, cover losses arising from:
- Vendor or supplier impersonation
- Executive impersonation
- Client impersonation.
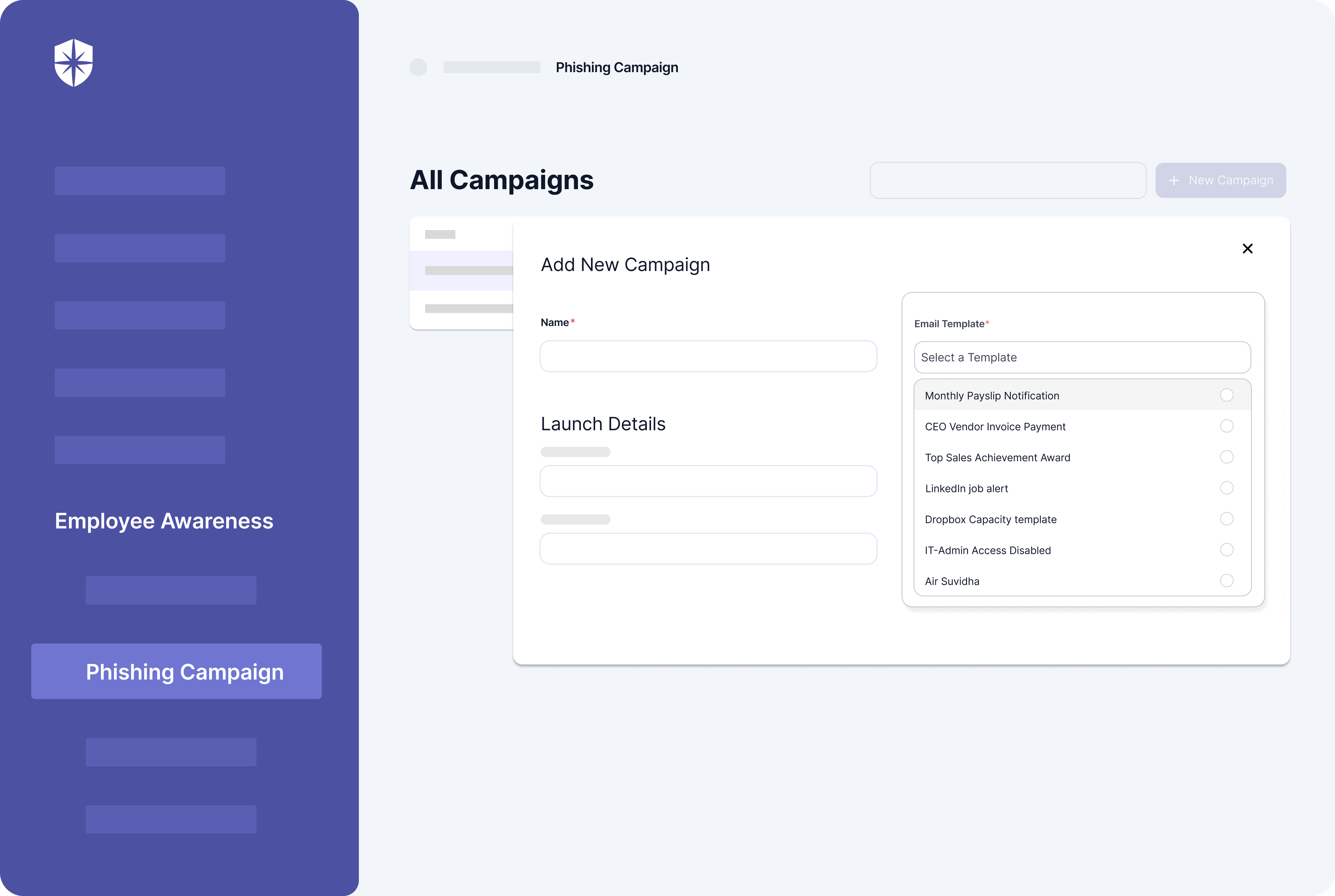
Across these threat areas, attackers get their way by playing with people’s psychology and phishing is on top of that list. So, a good defense strategy, which also improves meeting policy requirements, is ongoing phishing training on various social engineering tricks.
Again, you can do this with Cyber Sierra:

How Cyber Sierra Streamlines Getting Cyber Insurance
As I’ve established, insurers are more willing to offer coverage to organizations that show proactive cybersecurity preparations.
Cyber Risk Researcher, Daniel Kasper, corroborates:


We designed Cyber Sierra’s interoperable cybersecurity suite with this in mind. In three steps, our platform helps you prepare proactively, as well as streamlines access to relevant cyber insurance policies.
1. Meeting Requirements by Getting Cyber Hygiene Right
Cyber hygiene demonstrates your company’s risk profile to insurers. It shows you follow data security best practices, thereby increasing an insurer’s confidence in covering your organization.
Here are crucial security controls for achieving that:
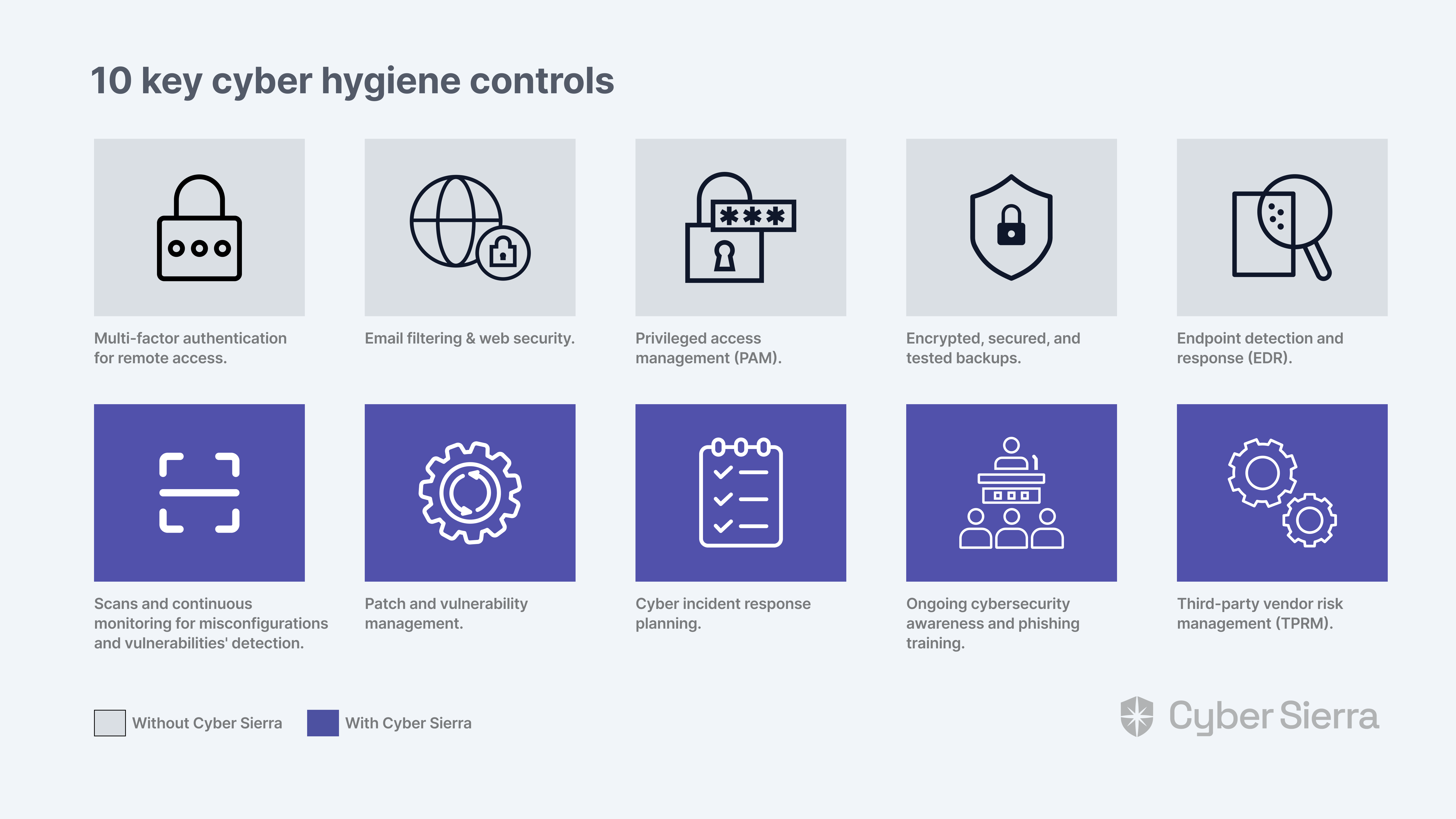

Five out of the 10 controls above are built into Cyber Sierra.
Take detecting misconfigurations and managing vulnerabilities. First, you can scan your cloud, repository, Kubernetes, Google Drive, and network systems in a few clicks. Our tool then ingests all the data into a dashboard:
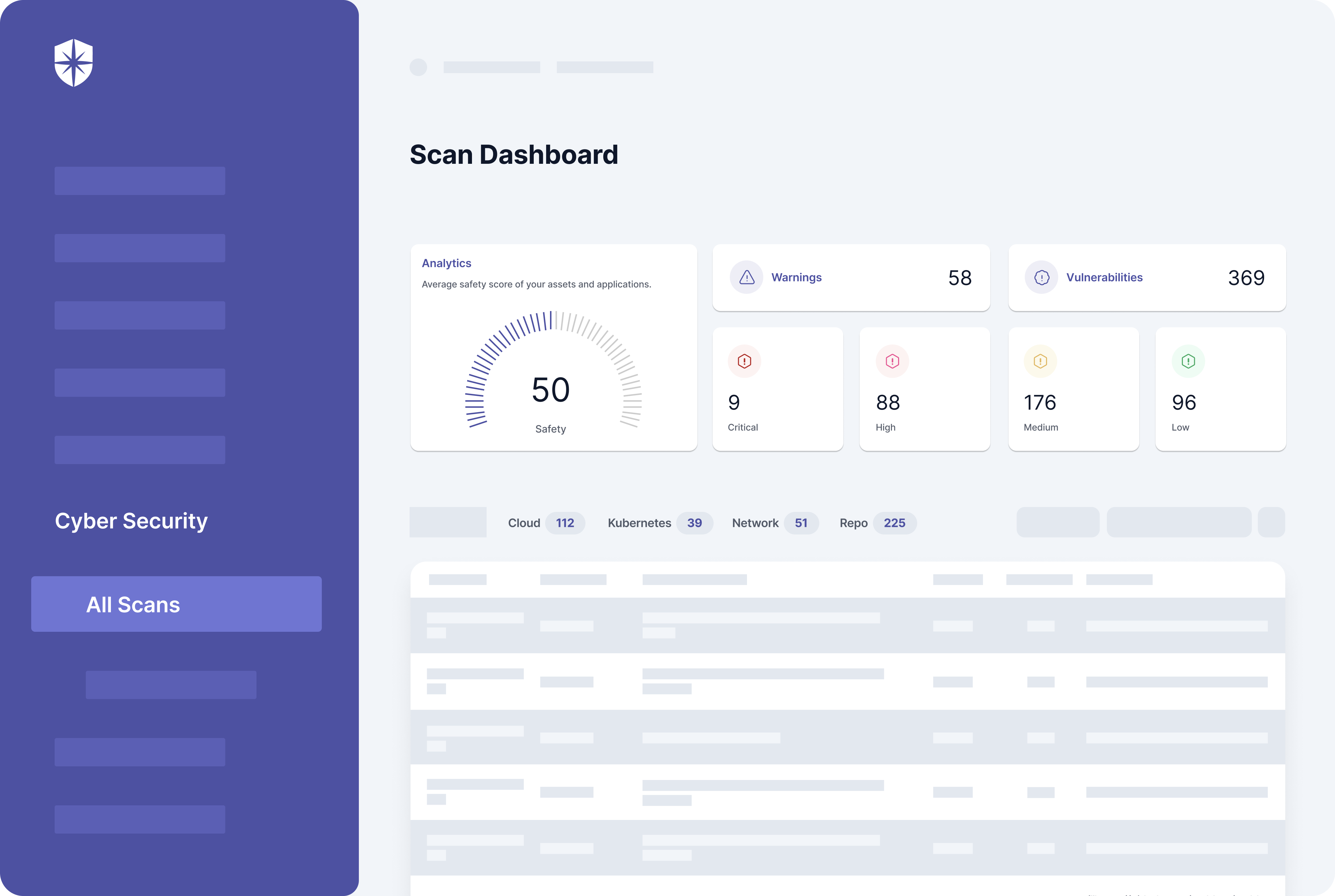

As shown in this security dashboard:
- Shows your company’s cybersecurity risk hygiene:
- Highlights security threats with succinct descriptions,
- Articulates remediation steps for each threat alert, and
- Lets your team assign remediation tasks or push to JIRA.
All these give your team a clear picture of specific risks to seek insurance coverage for, ensuring that you only buy what you need.
2. Collaborating with Teammates to Fill Insurance Forms
First, companies can access well-defined cyber insurance coverages right on the Cyber Sierra platform:
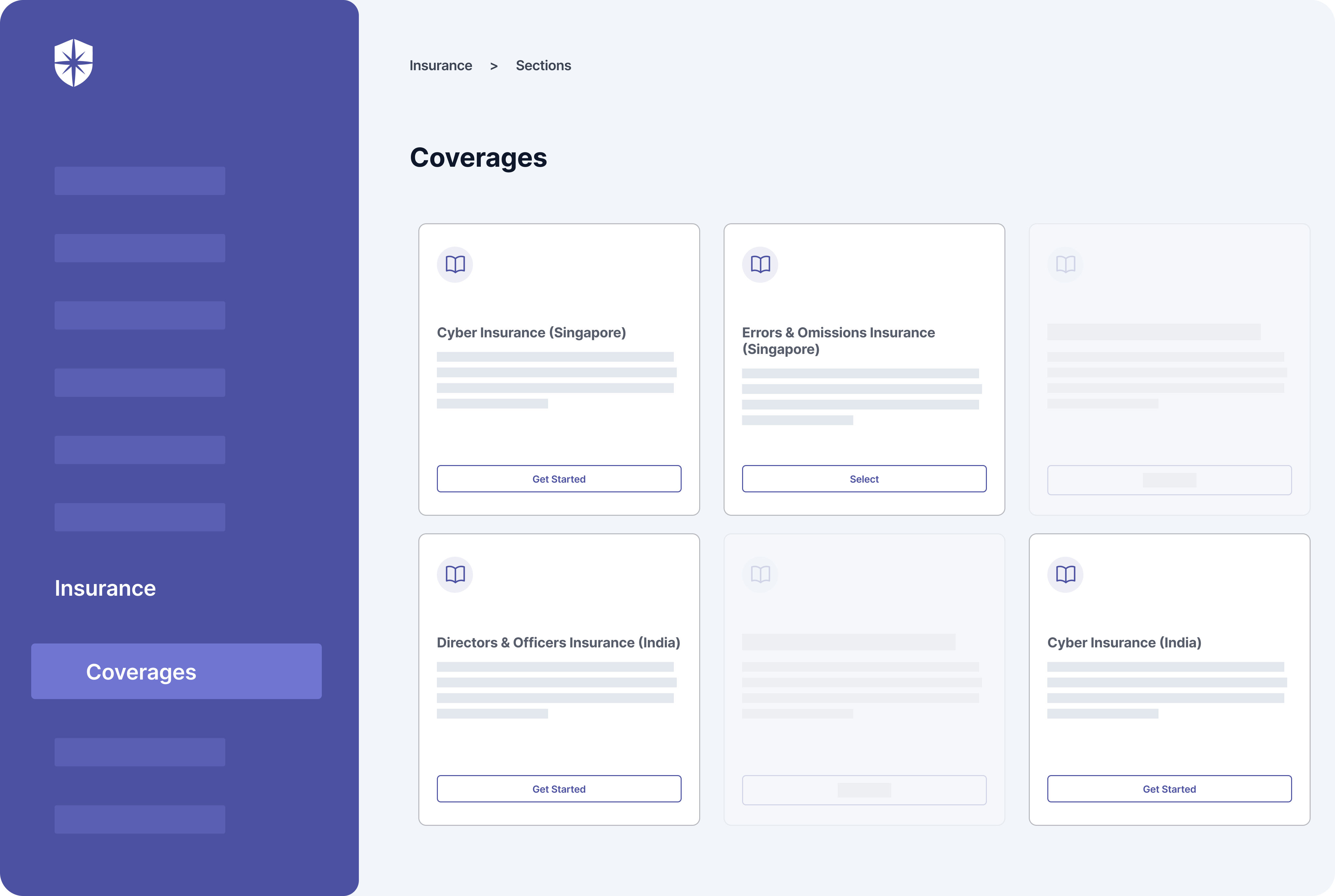

We’re adding more coverage as they become available.
But it doesn’t end there.
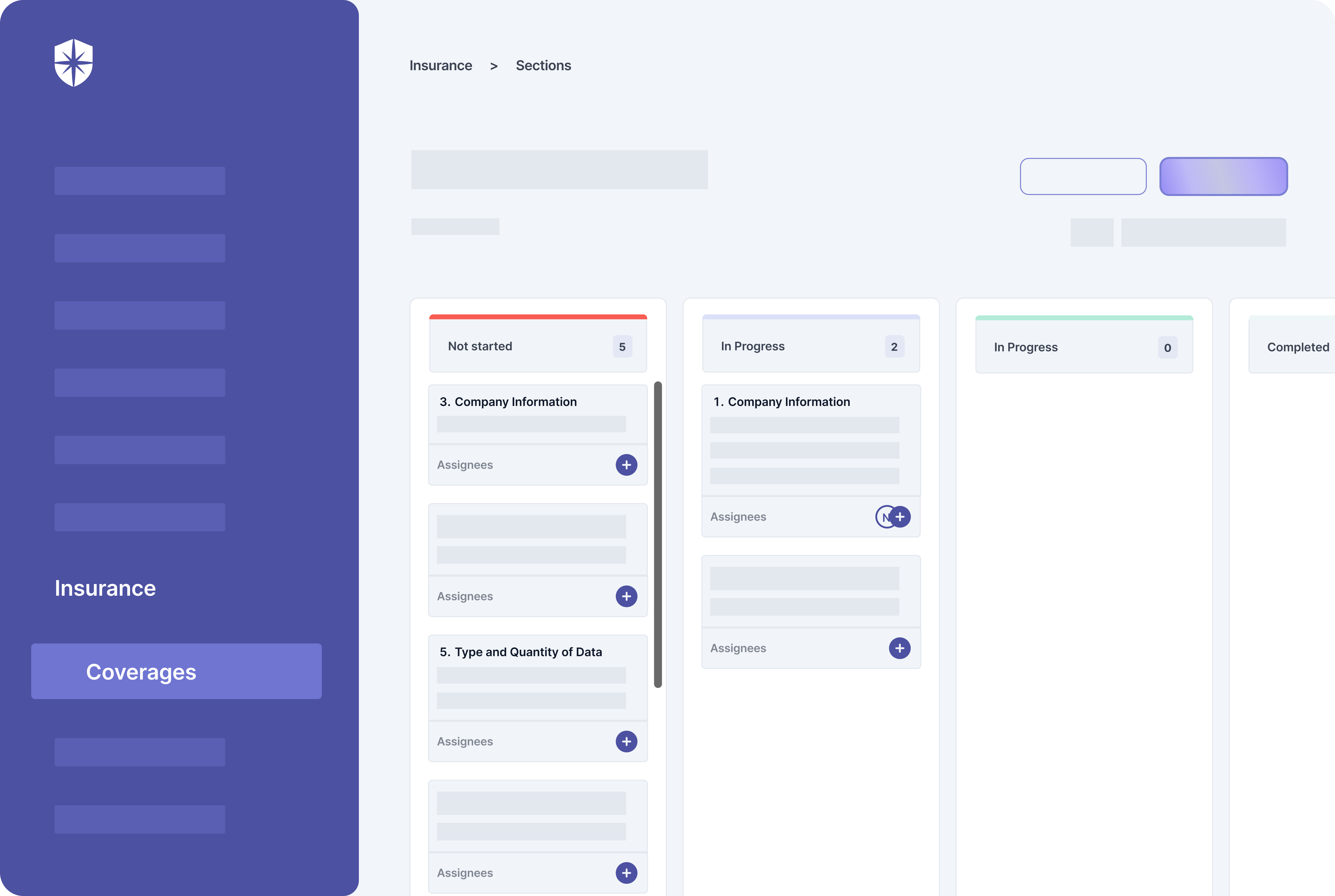
We know applying for cyber insurance can be a daunting task. So to ease the process for IT executives, Cyber Sierra enables collaborative form filling. Every insurance coverage on our platform is broken down into categories with the required info for each bucketed into tasks.
Executives can assign each of these tasks to relevant teammates and manage the entire process like a project arranged in a Kanban view:

3. Ensuring Evidence of Commitments is in Place
Recall that insurers mostly cover companies with solid cybersecurity controls. That doesn’t change once you start paying premiums. To qualify for reimbursements, insurance providers will require an audit of your company’s IT environment to verify claims.
This means your company must regularly ensure evidence of commitments to prepare for a claims’ event. And to do this, crucial things to do are:
- Restrict access to sensitive info,
- Document an incident response plan,
- Implement continuous risk assessment,
- Launch ongoing employee awareness training.
As shown earlier, launching and managing ongoing employee security awareness training takes a few clicks on Cyber Sierra. Our product also has a built-in risk register that monitors your security controls continuously:
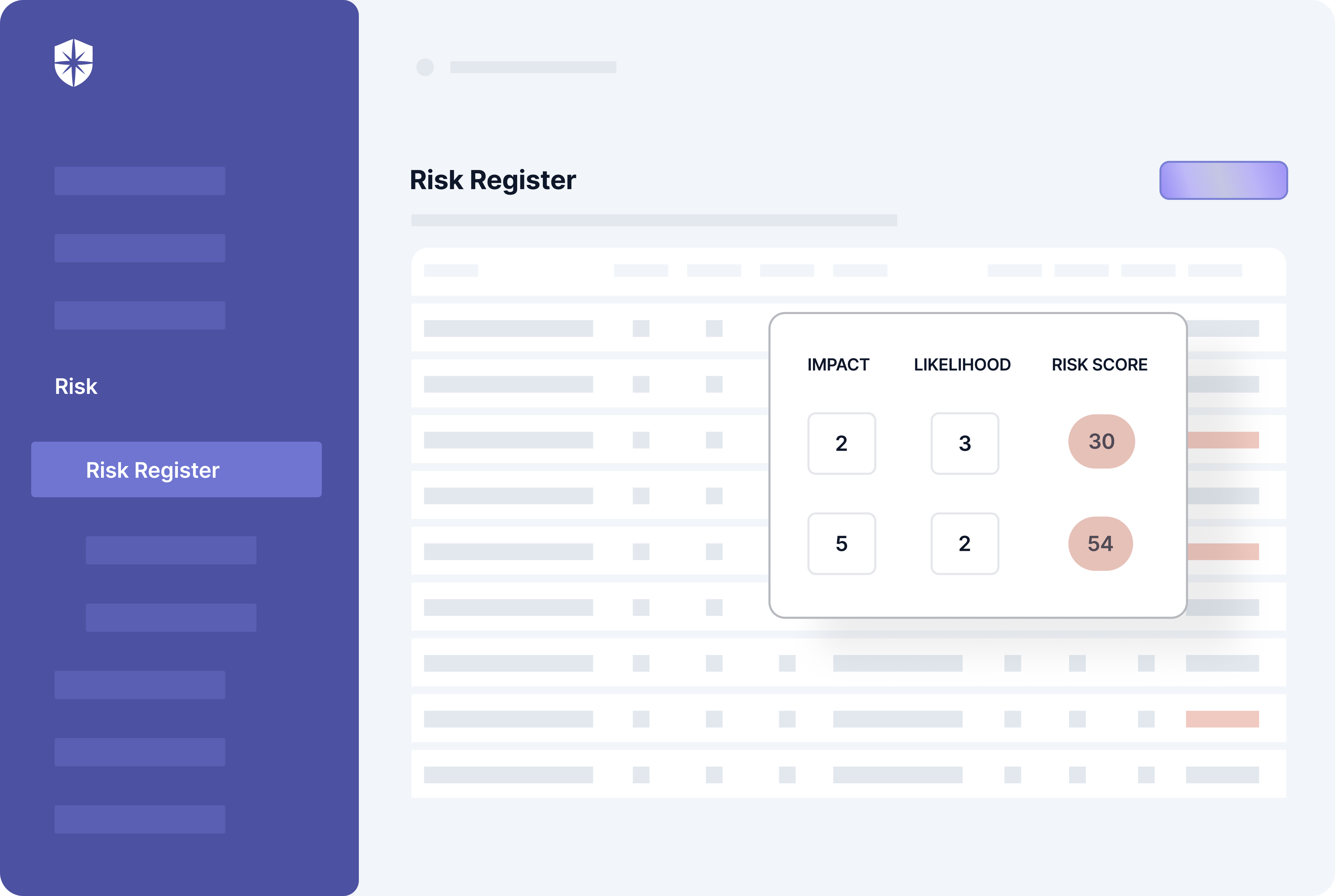

Right-Size Cyber Insurance, From One Place
Cyber insurance isn’t a silver bullet.
Good cyber resiliency requires that, even with insurance coverage, a solid cybersecurity system must still be put in place. This ensures continuous data security controls monitoring of threat alerts.
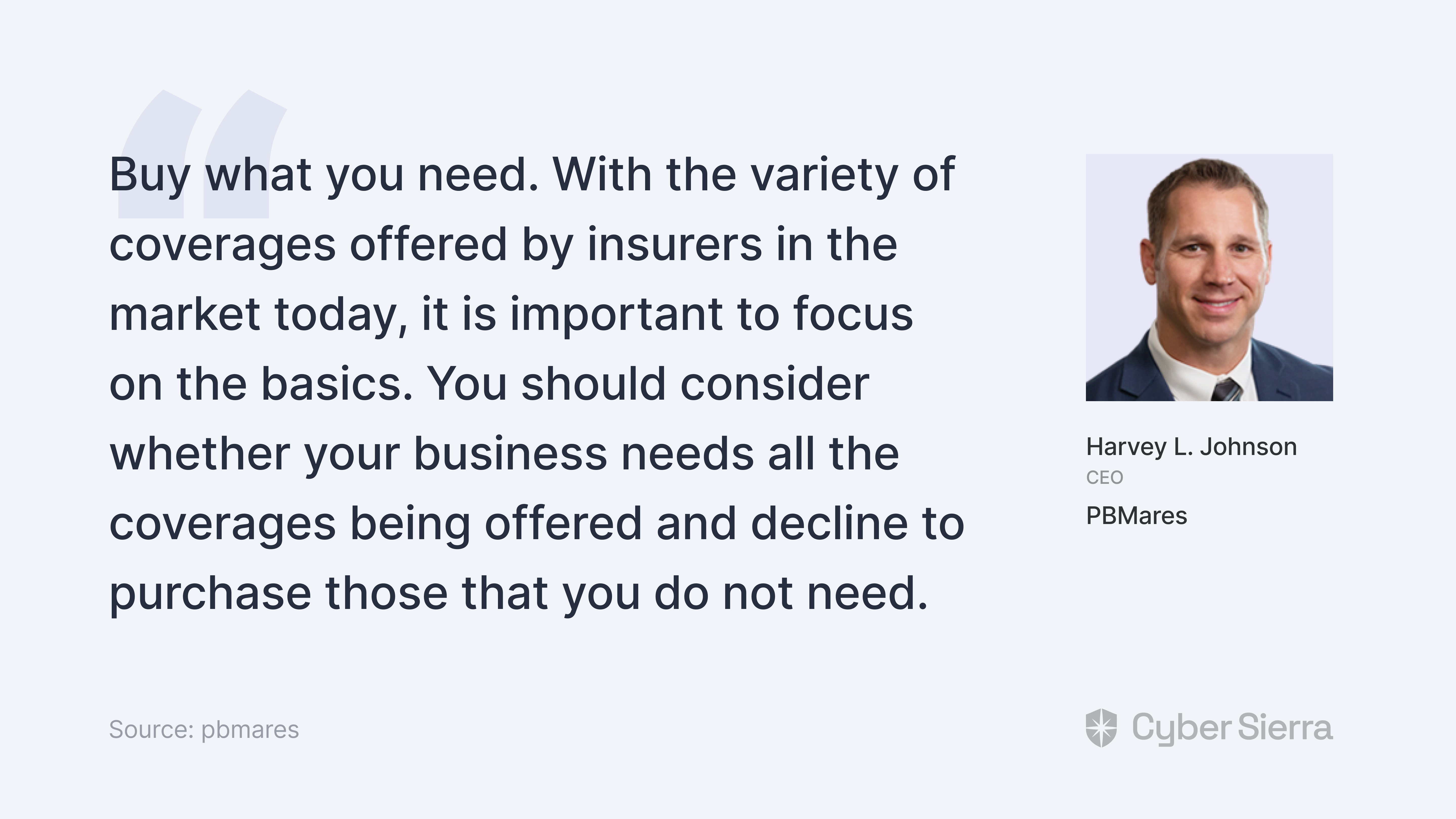
It also has the added advantage of guiding you to buy coverage your company actually needs. And that’s an important step in right-sizing cyber insurance, as the CEO of PBMares observed:

Cyber Sierra helps on both fronts.
The solutions needed to build a solid cybersecurity system work interoperably on our platform. And when the need to buy cyber insurance arises, you can find and apply collaboratively for what you need, too:




A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.