Why Is Multi-Factor Authentication Important?




Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
In today’s rapidly evolving digital landscape, ensuring the security of your accounts and sensitive data is more crucial than ever.
Organizations can no longer rely on traditional security measures alone, as it’s vulnerable to a myriad of cyber threats.
The solution? Multifactor authentication (MFA). It’s the most effective way to stop cybercriminals from accessing your data and systems.
But what exactly is MFA, and why has it become such a crucial element of modern cybersecurity?
In this article, we’ll examine MFA, how it works, and why it’s more secure than traditional login methods.


What is Multifactor Authentication?
Multifactor authentication is a type of authentication that requires users to provide more than one verification factor to access a resource like an application, online portal or an account. This can include a personal identification number (PIN) sent to your phone, a password generated by an app on your mobile device, or a one-time code from an authenticator app.
In short, when two or more forms of authentication are used—such as a password followed by an SMS message—it is called multifactor authentication.
Types of Multifactor Authentication
There are three main types of MFA. Let’s dive into these categories to understand better how MFA works.
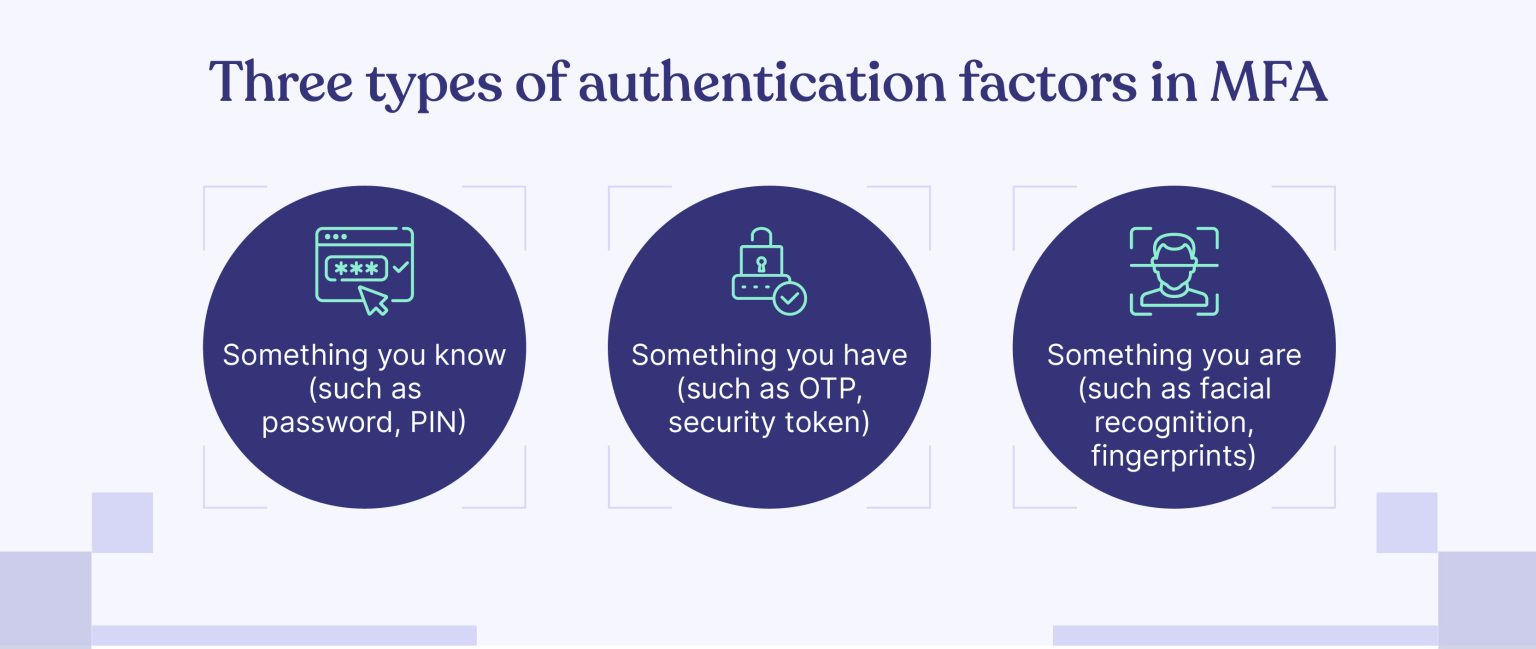

- Something you know: This is typically a password or a personal identification number (PIN). Creating strong, unique passwords and avoiding using the same password across multiple platforms is essential.
- Something you have: Something you have can be physical, like a security token, or digital (such as an OTP sent via text message).
- Something you are: This category includes biometric authentication methods, such as fingerprint scanning, facial recognition, or voice recognition. These methods are becoming increasingly popular due to their convenience and increased security.
Why is MFA Important?
MFA is important because relying solely on passwords and security questions to safeguard online accounts is no longer adequate. Cybercriminals can easily exploit weak passwords or trick users into revealing sensitive information through phishing attacks. Moreover, security questions can be compromised by attackers who have access to personal details about you.
Multifactor authentication offers an additional layer of protection, making it significantly harder for unauthorized individuals to breach your accounts.
The primary advantage of implementing MFA, therefore, lies in its ability to fortify an organization’s security posture by surpassing the limitations of traditional username and password combinations. Organizations can further streamline the user experience by offering a range of factors to choose from or by only mandating additional factors when necessary.
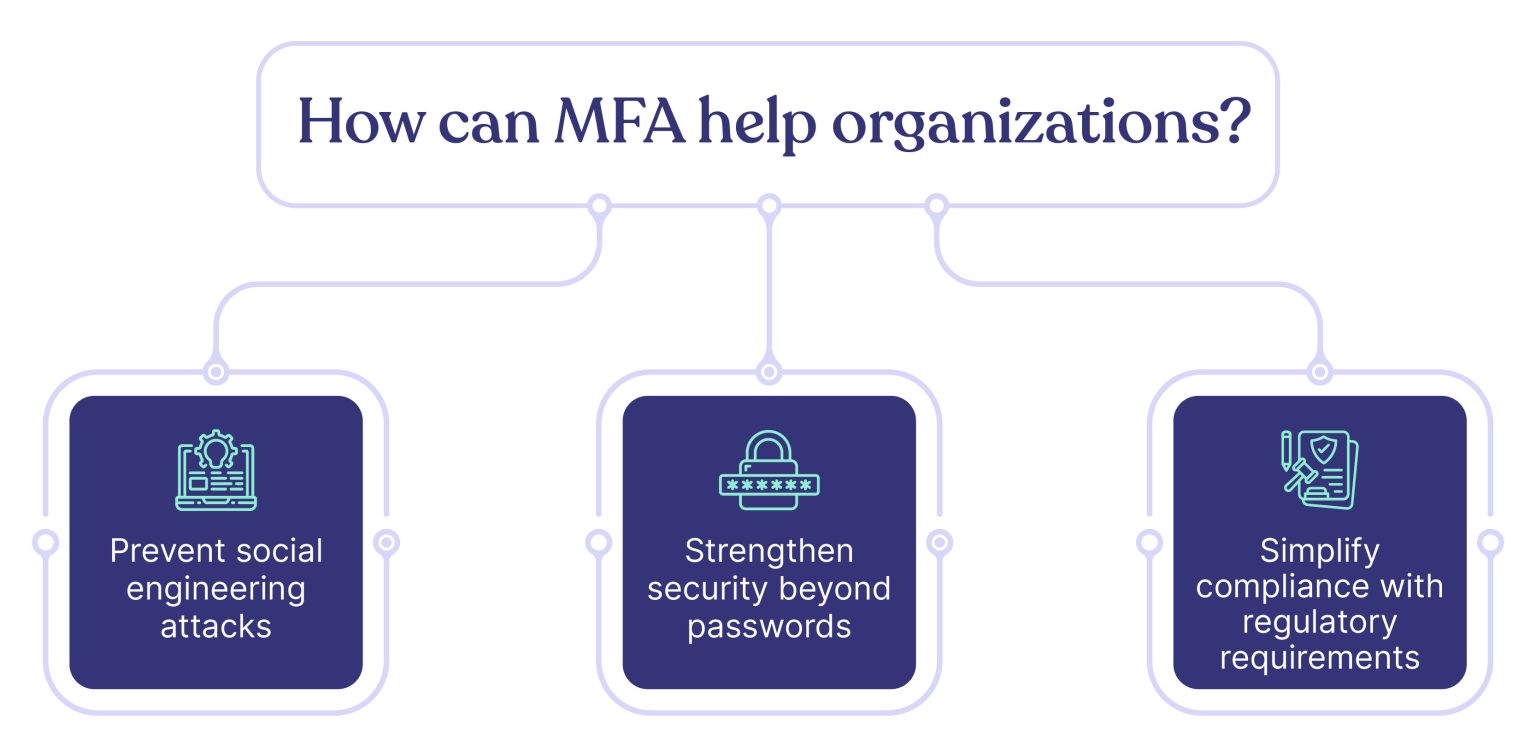

MFA is important because it helps organizations:
-
- Prevent social engineering attacks
- Strengthen security beyond passwords
- Simplify compliance with regulatory requirements
Let’s look at these in detail now.
1. Prevent social engineering attacks
One of the primary reasons MFA has become indispensable is the growing prevalence of social engineering attacks.
90% of cyber attacks involve social engineering tactics, and cybercriminals increasingly rely on tactics such as phishing and impersonation to deceive employees and gain unauthorized access to sensitive data. These attacks often exploit human weaknesses rather than technical vulnerabilities, making them challenging to prevent.
MFA is a powerful deterrent to social engineering attacks by requiring users to provide multiple verification forms before granting access to a system.
Even if an attacker obtains a user’s login credentials through a phishing scam, they would still need to bypass the additional authentication factors, such as a one-time password or biometric data, significantly reducing the likelihood of a successful breach.
2. Strengthen security beyond passwords
Despite the well-known risks associated with weak passwords, many employees continue to use easily guessable or reused passwords across multiple accounts. As a result, 30% of internet users have experienced a data breach.
MFA helps mitigate this risk by adding layers of security beyond the traditional username and password combination.
With additional authentication factors, such as something you have (like a token) or something you are (such as a fingerprint), MFA makes it exponentially harder for attackers to gain unauthorized access.
3. Simplify compliance with regulatory requirements
Organizations operating in regulated industries, such as finance and healthcare often face stringent security requirements to protect sensitive data.
Such organizations can meet these requirements by demonstrating a commitment to robust security practices.
Incorporating multifactor authentication into your cybersecurity strategy will add more resilience to your your business and help mitigate the impact from data breaches, reducing the chances of regulatory fines and damage to reputation.
How Does MFA Work?
MFA works through a multi-layered approach that requires users to provide two or more authentication factors to gain access to their accounts. It requires you to provide multiple pieces of information or use different methods to prove it’s really you. This information is then saved safely in the system for future logins to make sure it’s really you accessing your account.
This is a straightforward yet powerful process to enhance security:
- Registration: Users link a personal item, such as a smartphone or key fob, to the MFA system, claiming ownership.
- Login: Users enter their username and password into the secure system.
- Verification: The MFA system communicates with the registered item, sending verification codes to smartphones or activating key fobs.
- Reaction: Users complete the authentication process using the registered item, such as entering the verification code or pressing a button on the key fob.
While some MFA systems require verification for every login attempt, others employ more flexible approaches. For example, a system may remember trusted devices or locations, skipping the verification step for subsequent logins from the same device or location.
However, if a user attempts to log in from a new device or at an unusual time, the system may trigger the MFA process to ensure security.
What Are the Benefits of Multifactor Authentication?
Here are the major benefits of multifactor authentication
- Enhanced security through layered protection
- Reduced risk of phishing attacks
- Improved user experience with adaptive authentication
- Streamlined access management with Single Sign-On integration
- Thwarted brute force attacks

Now let’s look at them in detail,
1. Enhanced security through layered protection
Multifactor authentication (MFA) significantly improves your organization’s security by adding multiple layers of protection.
Instead of relying solely on a password, multifactor authentication requires additional factors like fingerprints or smartphone apps to verify a user’s identity. This can block over 99.9% of account compromise attacks.
This makes it much more difficult for cybercriminals to access your systems, as they would need to compromise multiple factors to gain unauthorized access.
2. Reduced risk of phishing attacks
MFA reinforces your organization’s defense against potential breaches and unauthorized access by implementing an additional layer of protection.
This security measure mandates users to provide supplementary forms of identification, adding an extra barrier that significantly enhances resilience against various cyber threats.
3. Improved user experience with adaptive authentication
Adaptive authentication is a unique and uncommon benefit of MFA that tailors the authentication process based on the user’s behavior and risk profile.
With adaptive authentication, users are prompted for additional factors only when their behavior deviates from their established patterns.
For instance, if a user tries to log in from a new location or device that hasn’t been used before, adaptive authentication may trigger an additional authentication step to ensure the user’s identity. However, if the user’s behavior aligns with their usual patterns, adaptive authentication may allow them to proceed with a streamlined login process, reducing unnecessary prompts for additional authentication factors.
This increases security and improves the user experience by reducing the number of times users are prompted for additional authentication.
4. Streamlined access management with Single Sign-On integration
MFA can seamlessly integrate with Single Sign-On (SSO) solutions to provide a streamlined and secure user experience. With SSO, employees can access multiple applications and services using a single set of credentials, reducing the need to remember multiple passwords.
Combining SSO with MFA creates a powerful, convenient security solution that simplifies access management while ensuring high protection against unauthorized access. This integration saves time for your employees and reduces the risk of password-related security breaches.
5. Thwarted brute force attacks
Brute force attacks involve repeated login attempts using various password combinations to gain unauthorized access to an account.
MFA effectively deters these attacks by requiring additional verification forms beyond just passwords. The increased difficulty of bypassing MFA means that cybercriminals are more likely to abandon their attempts, leaving your organization’s data secure.
How Does MFA Strengthen Cybersecurity?
Implementing MFA heightens the difficulty for threat actors attempting to gain access to the system. It accomplishes this by requiring the provision of two or more factors to verify a user’s identity and grant them access to an account.
With MFA in place, there is a reliable assurance that only authorized users, who can successfully provide the required factors, are granted access.
MFA also offers a unique advantage: contextual awareness.
This means that MFA systems can analyze and adapt to user behavior, location, and device, making it more difficult for cybercriminals to bypass security measures. By leveraging contextual awareness, MFA can provide an additional layer of protection that traditional security measures may not offer.
For example, consider a scenario where an employee logs in to a secure system using their username and password. If a cybercriminal were to obtain this information, they could easily access the system.
However, with MFA in place, the system would require the user to provide an additional form of identification, such as a fingerprint, a one-time passcode sent to their mobile device, or even a physical security token. This added layer of security makes it significantly more challenging for cybercriminals to gain unauthorized access.
According to Google, MFA can also block around 99.9% of automated bot attacks. Bots cannot intercept the codes generated by MFA, and humans trying to bypass prompts will fail unless they use highly sophisticated methods to do so—or try a brute-force attack (attempting every possible combination). With two-factor authentication, a stolen password or PIN cannot be used to gain access.
How to Choose an MFA Solution?
Here are the six main tips for choosing the right MFA solution for your organization:
- User-friendly authentication methods
- Streamlined onboarding process
- Ease of integration
- Robust reporting and analytics
- Scalability and flexibility
- Strong customer support

Let’s explore them one by one.
1. User-friendly authentication methods
Offering a variety of user-friendly authentication methods is vital for accommodating different user preferences and situations.
Some employees may prefer using biometric authentication, such as fingerprint or facial recognition, while others might opt for a hardware token or SMS-based authentication. Offering various options enables you to accommodate your employees’ diverse preferences and needs.
2. Streamlined onboarding process
Deploying MFA will be a major step forward in protecting your organization against account takeover and data loss—but it’s crucial that the solution you choose can be easily deployed across all of your corporate applications.
MFA deployment can be complex, with time-consuming configurations needed to onboard users across your different applications. Even worse, things may go wrong with the wrong solution. That’s why we recommend only MFA solutions that offer a streamlined onboarding process.
When evaluating MFA solutions, look for those with clear instructions, simple layouts, and minimal steps required for initial setup and configuration. This reduces the learning curve and ensures that users can quickly and efficiently complete the authentication process.
3. Ease of integration
Another critical factor in choosing an MFA solution is the ease of integration. Look for a solution that offers straightforward setup and configuration processes and clear documentation and support resources.
The easier it is to integrate the MFA solution with your existing systems, the faster your organization can enjoy the enhanced security benefits. Also, ensure that the MFA solution you’re considering is compatible with your organization’s existing systems and applications.
This includes your operating systems, email clients, VPNs, and other critical infrastructure components. Compatibility with your current systems is vital to minimizing disruptions during implementation and ensuring a smooth transition for your employees.
4. Robust reporting and analytics
Having access to detailed reporting and analytics is crucial for monitoring the effectiveness of your MFA solution and identifying potential security risks. The admin console should provide straightforward access to reports.
While evaluating a solution, pay attention to the comprehensiveness of the information displayed and the simplicity of generating, scheduling, and retrieving reports. Reports need to be conveniently located and exportable, enabling you to access all necessary data promptly.
While you may need to create reports tailored to your organization’s requirements, it is advisable to choose a solution that offers fundamental features such as comprehensive summaries of user deployment, lockouts due to failed login attempts, security incidents, and in-depth authentication logs
Choose an MFA solution that offers comprehensive reporting and analytics tools, including real-time visibility into authentication events, user behavior, and potential threats.
These insights can help you make informed decisions about your organization’s security posture and identify areas where additional training or support may be needed.
5. Scalability and flexibility
As your organization grows and evolves, your MFA solution should be able to adapt and scale accordingly. Choose an MFA solution that can easily accommodate an increasing number of users, devices, and applications without compromising security or performance.
In addition, look for a solution that offers flexibility in terms of customization and configuration. This allows you to tailor the MFA solution to your organization’s unique needs and requirements, ensuring the best possible user experience and security outcomes.
6. Strong customer support
Lastly, consider the level of customer support offered by the MFA solution provider. Implementing and managing an MFA solution can be challenging, and having access to knowledgeable and responsive support resources can make all the difference.
When evaluating MFA solutions, look for providers that offer multiple support channels, such as phone, email, and live chat, as well as extensive knowledge bases and self-help resources. This ensures that you have access to the assistance you need when you need it.
Wrapping Up
In conclusion, Multifactor Authentication (MFA) is crucial to any organization’s cybersecurity strategy. Due to the extra level of security, MFA can help you avoid phishing attacks. It also makes compliance with regulatory requirements easier.
Although MFA is a relatively simple solution, implementing it properly takes time. This is why choosing a provider that offers cost-effective, efficient, and easy-to-use solutions is important. This way, you can focus on other important aspects of your business while ensuring your users are protected.
Cyber Sierra’s employee security training program focuses on many such relevant and critical security measures that individuals can implement to protect themselves from data breaches and security incidents.
Book a demo with us to know how you can implement a comprehensive employee security training program with us.
Frequently Asked Questions
1. What are the three types of authentication factors?
The three types of authentication factors are: something you know (such as a password or PIN), something you have (such as a token or bank card), and something you are (such as biometrics like fingerprints or voice recognition). These three types of factors provide different layers of verification, ensuring a more robust and secure authentication process.
2. Is multi-factor authentication the same as OTP?
No, MFA isn’t the same as OTP even though OTP (One-Time Password) is a form of multi-factor authentication (MFA). MFA is a broader concept that encompasses various methods of requiring additional credentials for authentication beyond just a password. It involves the use of multiple factors, such as something the user knows, something they have, or something they are, to verify their identity.
3. How safe is multi-factor authentication?
Multi-factor authentication significantly enhances the security of user accounts and makes it substantially more difficult for malicious actors to compromise them. The primary reason for this increased safety is the additional layer of protection MFA provides, even if one factor, such as a password, is compromised.


A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.